-
Provisioning Services 7 and Server 2012 Group Managed Service Account
June 29, 2013
Citrix released Provisioning Services version 7 (PVS7) with support for running on Microsoft Windows Server 2012. Server 2012 has a really nice new feature called Group Managed Service Accounts (gMSA). Even though Citrix had to test installing PVS7 on Server 2012, I found that Citrix never tested using gMSA for the Stream or SOAP services. This article is my attempt to see if PVS7 will allow a gMSA for the Stream and SOAP services.
I have absolutely no idea if PVS7 running on Server 2012 will work with a gMSA or not. Citrix says it should work, but the articles I have read from Microsoft make it seem like the application must be written to support and work with gMSA. You will find out at the same time I do whether this experiment will work.
To get more information on gMSA, please read this TechNet article.
There are three requirements to use a gMSA:
- At least one Windows Server 2012 Domain Controller.
- A Windows Server 2012 or Windows 8 computer with the ActiveDirectory PowerShell module to create/manage the gMSA.
- A Windows Server 2012 or Windows 8 domain member to run/use the gMSA.
I installed a Server 2012 Domain Controller into my lab environment, using it to create and manage the gMSA.
Step 1: Create the Key Distribution Services (KDS) Root Key
The KDS Root Key is used by the KDS service on the domain controller to generate passwords. On my Server 2012 Domain Controller, I will run from an elevated PowerShell session:
Add-KDSRootKey –EffectiveImmediately
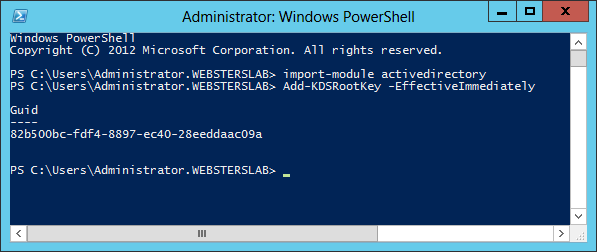
Figure 1 The TechNet article says the key can take up to 10 hours to replicate and take effect. Since I only have one Server 2012 domain controller and two domain controllers in my lab, I am not worried about the replication time. By the way, it took almost one hour in my lab before the key was usable!
Step 2: Create and configure the gMSA
I am going to create a Security Group containing my two PVS7 servers. This security group will contain the computer accounts allowed to use the gMSA.
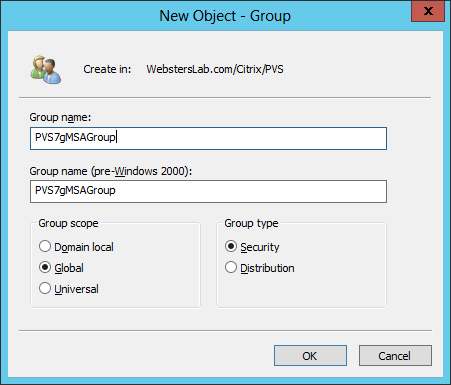
Figure 2 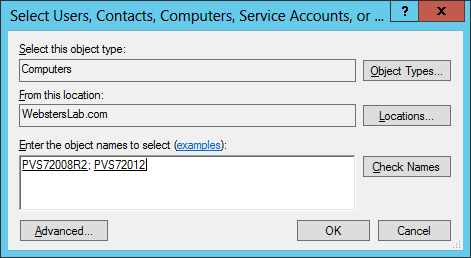
Figure 3 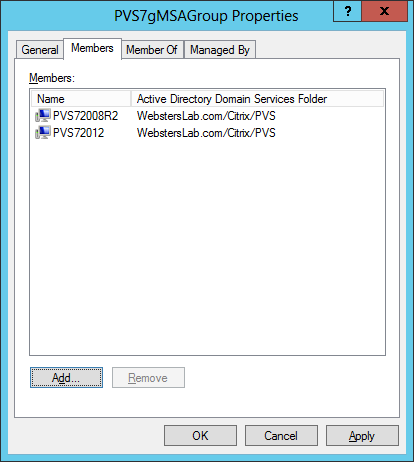
Figure 4 Next, my two PVS7 servers need to be restarted to know they were added to the security group.
From the elevated PowerShell session on my Server 2012 domain controller, I run:
New-ADServiceAccount –Name PVS7StreamSOAP –DNSHostName PVS7StreamSOAP.websterslab.com –PrincipalsAllowedToRetrieveManagedPassword “PVS7gMSAGroup”
Note: The Name is a NetBIOS name that must not be more than 15 characters.
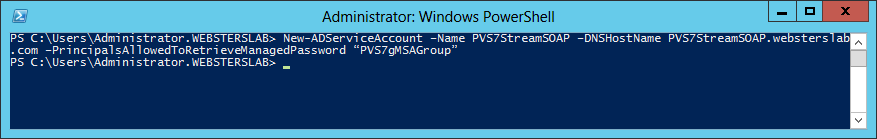
Figure 5 The gMSA now appears in the Managed Service Accounts OU in Active Directory Users and Computers.
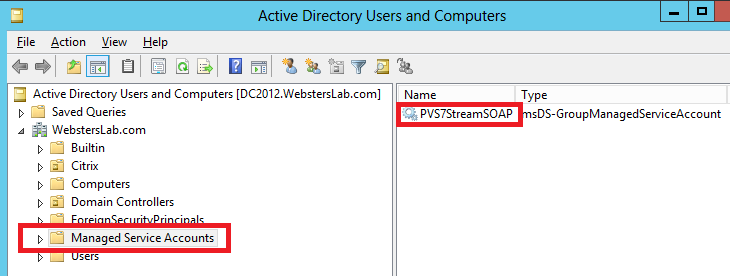
Figure 6 Step3: Configure the gMSA on the PVS7 host
Note: The following requires the Active Directory module for Windows PowerShell to be installed on the PVS7 host. It can be uninstalled after the test is successful.
From an elevated PowerShell session on the PVS7 server, I will run the following two cmdlets:
123Install-AdServiceAccount PVS7StreamSOAPTest-AdServiceAccountPVS7StreamSOAP
Figure 7 The Test-AdServiceAccount should return True. If it returns False, a verbose error message should be included.
Now for the time of truth. Is this going to work in PVS7 or not. Start the Provisioning Services Configuration Wizard and go to the User account screen. The TechNet article says the trick is to use a “$” after the gMSA and leave the password blank.
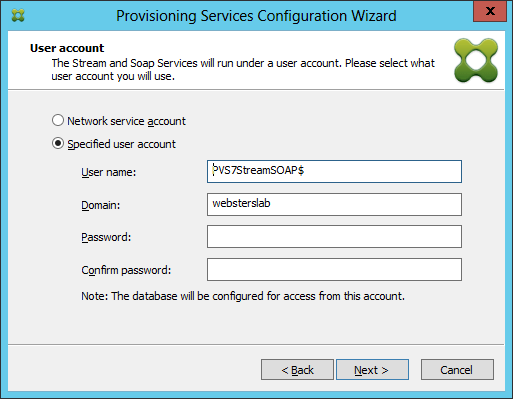
Figure 8 Let’s see what happens when I click Next?????
What do you know, it let me continue, but we are not done yet.
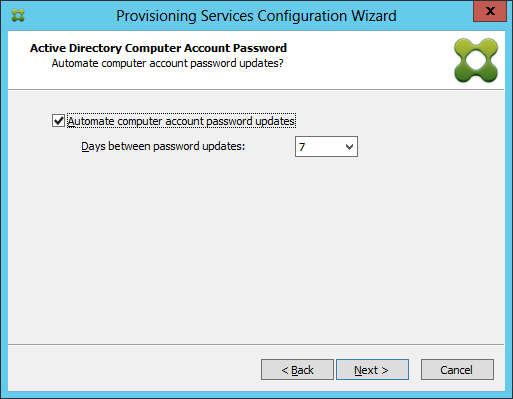
Figure 9 DOH!!! I guess PVS7 will NOT work with Server 2012’s Group Managed service Accounts after all! Total Bummer.
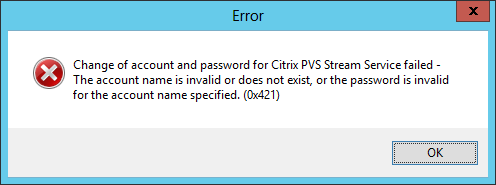
Figure 10 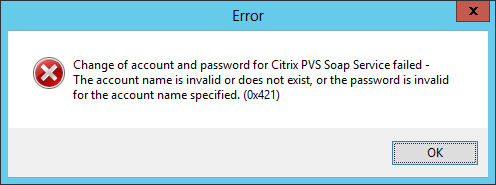
Figure 11 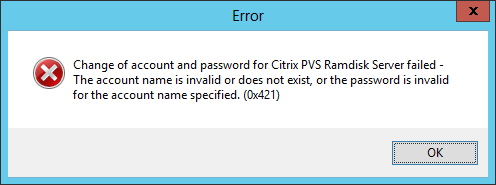
Figure 12 Citrix should fix this pronto. Actually, this should have been in PVS7 from the initial design for Server 2012 support. gMSA offers several features that would be very useful in a PVS implementation. Too bad Citrix doesn’t support gMSA at this time. I hope this gets fixed fast.
Thanks
Webster
2 Responses to “Provisioning Services 7 and Server 2012 Group Managed Service Account”






October 4, 2016 at 11:28 am
Hi Carl,
since this article is indeed already a bit older, I would like to know if you’ve looked at the issue again.
Best regards,
Lars
October 4, 2016 at 12:28 pm
I have not but another CTP did and said they now work.
Webster