-
New Script: Update Active Directory DNS Reverse Lookup Zones from Sites and Services Subnets (Update-ReverseZonesFromSubnets.ps1)
April 20, 2020
While Active Directory (AD) does not need DNS Reverse Lookup Zones, most Citrix and VMware products do. If you are visiting my website, you probably use Citrix and VMware products. If you have heard or read any of my AD conference or CUGC presentations, you know how important AD Sites and Services Subnets and DNS Reverse Lookup Zones are to Citrix and VMware.
This script was written specifically for a customer to help them with keeping their DNS Reverse Lookup Zones in sync with their Subnets. The customer’s CIO stated the script was useful to them, so it would be useful to the community. The CIO wanted this script made available to the community.
If you would like to thank this CIO for the generous gift, send an email to Webster at carlwebster dot com, I will gather up the responses and send them to the CIO.
I also want to thank all the testers. My always detailed and thorough tester David M., fellow CTP Trond Eirik Haavarstein (aka Mr. XenAppBlog), the testers from the IGEL Slack Community, and the World of EUC Slack Community.
What does this script do?
- Get all the Subnets defined in Sites and Services
- Sort the Subnets
- Change the Subnet to a format that resembles a DNS Reverse Lookup Zone
- See if a matching Reverse Lookup Zone exists
- If the reverse zone does exist, there is nothing to do
- If the reverse zone doesn’t exist, depending on whether -WhatIf or -Confirm is used, create the Reverse Lookup Zone
- Log everything done
- Create a text file of all actions
- Optionally, email the text file
The first problem encountered, was the difference in how Subnets and Reverse Lookup Zones are stored.
Let’s look at Subnets for 10.0.0.0/8, 172.16.0.0/16, 192.168.168.0/24, and 192.168.168.168/32, as shown in Figure 1.
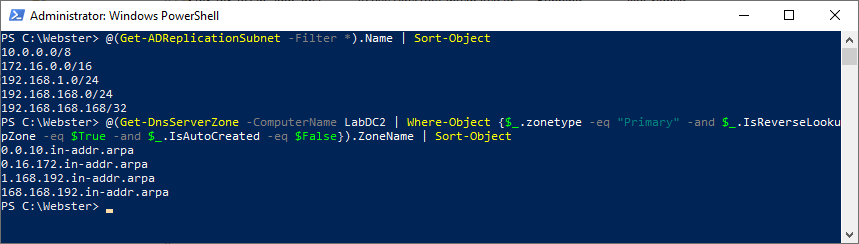
Figure 1 Subnets as stored as a.b.c.d/nn and a reverse zone is stored as c.b.a.in-addr.arpa.
It is a simple task of splitting the Subnet into an array and then creating a temp zone with:
12345678910111213141516171819$SubnetArray=$Subnet.split("./")$SubnetMask=[int]$SubnetArray[($SubnetArray.count-1)]If($SubnetMask-le8){$RevZone= "$($SubnetArray[0]).in-addr.arpa"}ElseIf($SubnetMask-le16){$RevZone= "$($SubnetArray[1]).$($SubnetArray[0]).in-addr.arpa"}ElseIf($SubnetMask-le24){$RevZone= "$($SubnetArray[2]).$($SubnetArray[1]).$($SubnetArray[0]).in-addr.arpa"}Else{$RevZone= "$($SubnetArray2[0]).$($SubnetArray[2]).$($SubnetArray[1]).$($SubnetArray[0]).in-addr.arpa"}Creating a reverse lookup zone is different. You create a reverse lookup zone by using the Subnet! For example, you create a reverse zone by using “192.168.1.0/24”, but you retrieve the reverse zone by using “1.168.192.in-addr.arpa”.
To show you what the script does, I deleted the Reverse Lookup Zones I created to get the screenshot for Figure 1.
Figure 2 shows my DNS before the script runs.
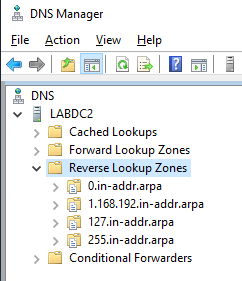
Figure 2 Figure 3 shows the script in action.
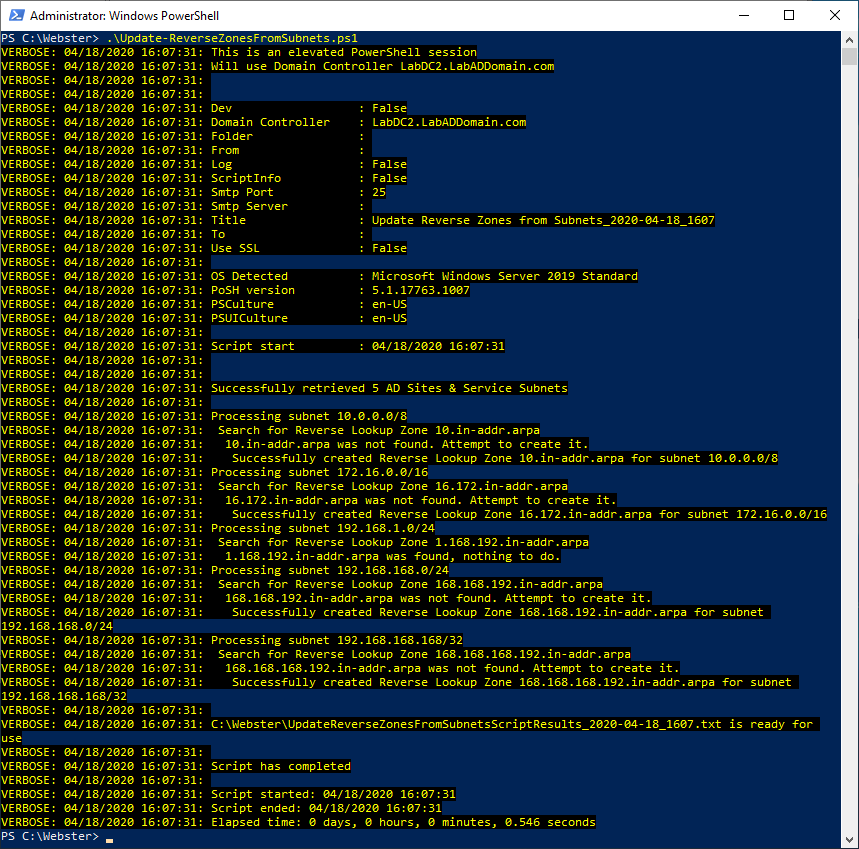
Figure 3 Figure 4 shows DNS after the script ran.
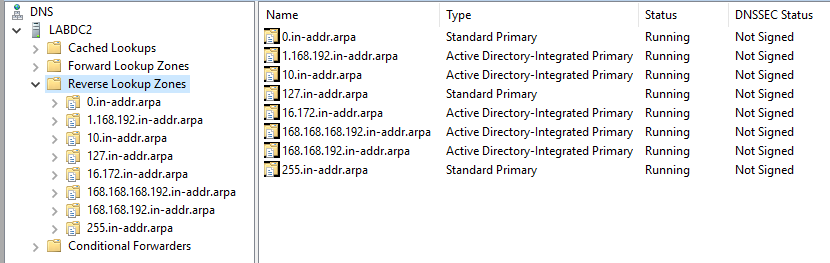
Figure 4 Note: You cannot create a /32 Reverse Lookup Zone in the DNS console, but I did with PowerShell.
Figure 5 shows the contents of the text file generated by the script.
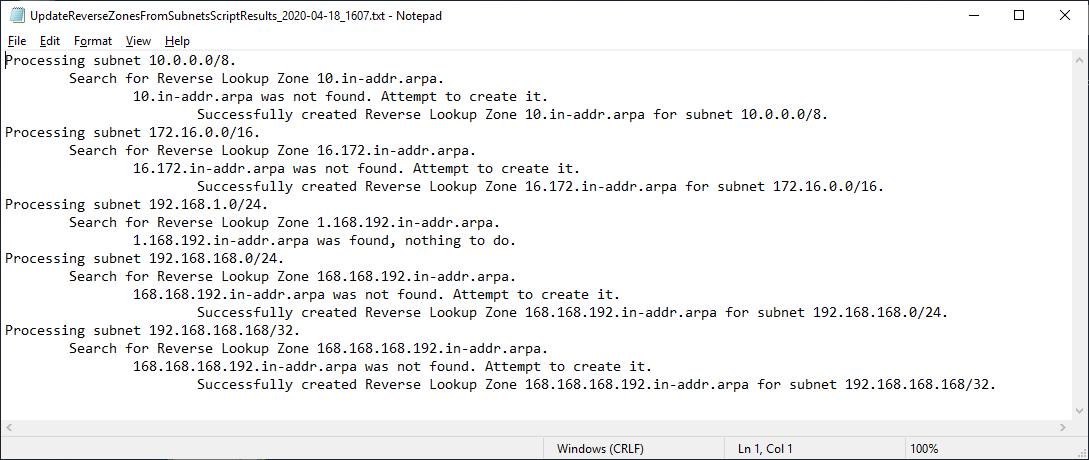
Figure 5 What happens if the script is rerun now that all the Subnets have DNS Reverse Lookup Zones? Figures 6 and 7 show what happens.
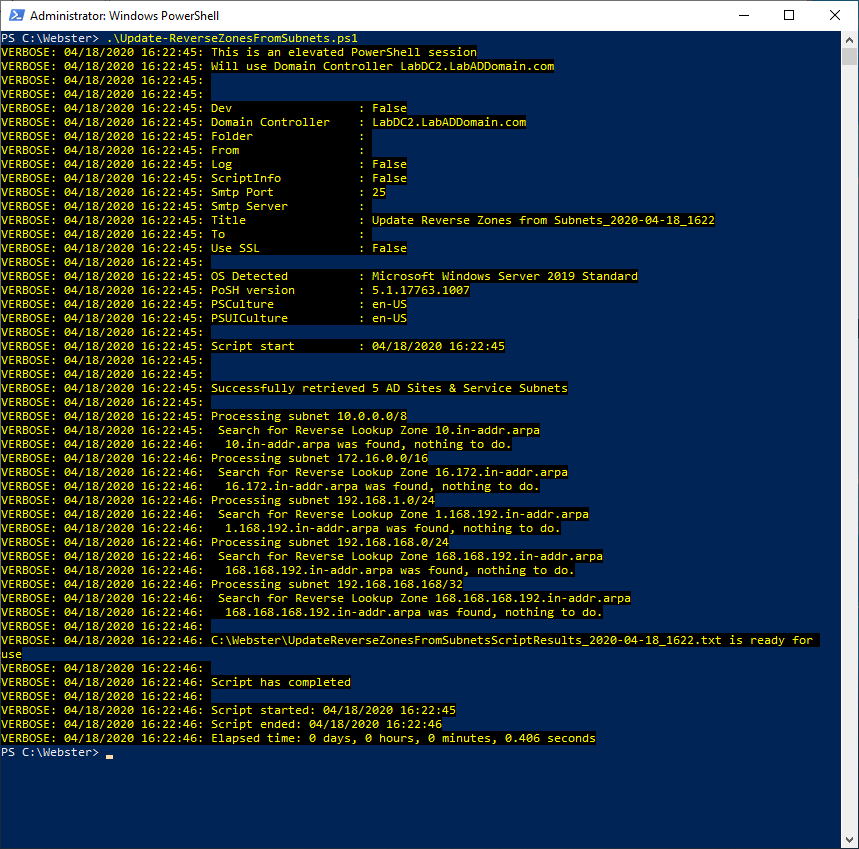
Figure 6 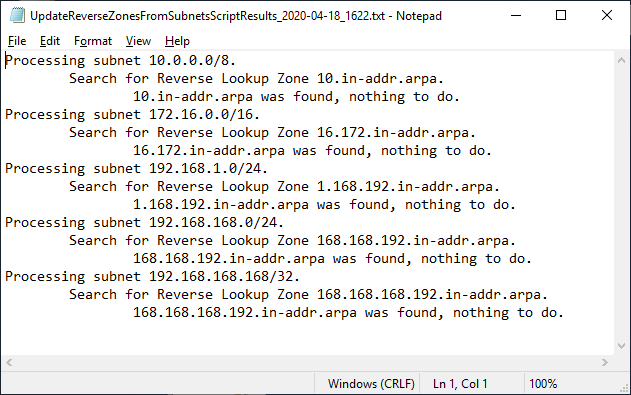
Figure 7 The script supports -WhatIf and -Confirm as shown in Figures 8 through 13.
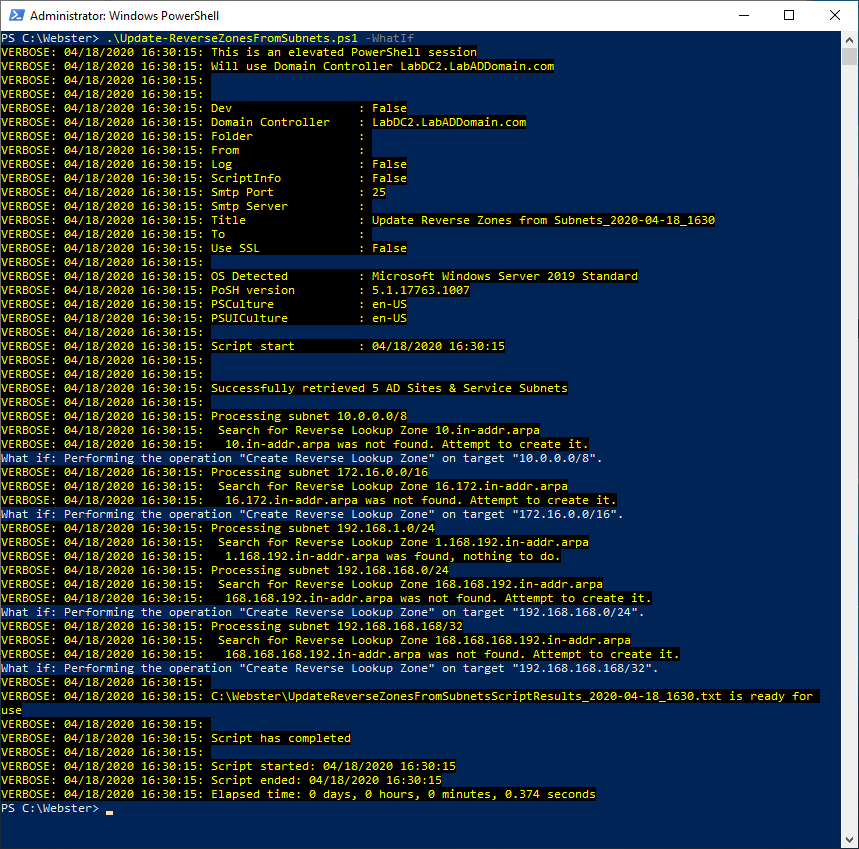
Figure 8 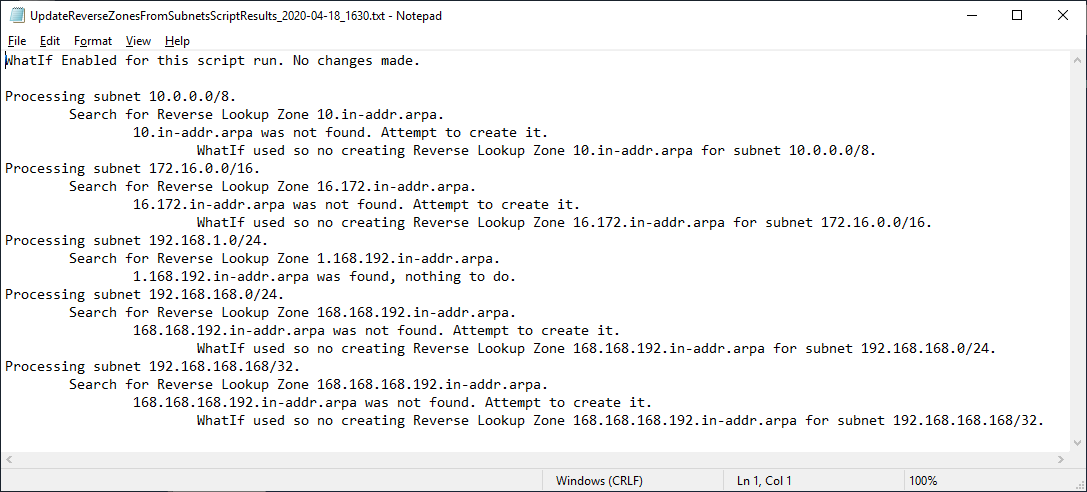
Figure 9 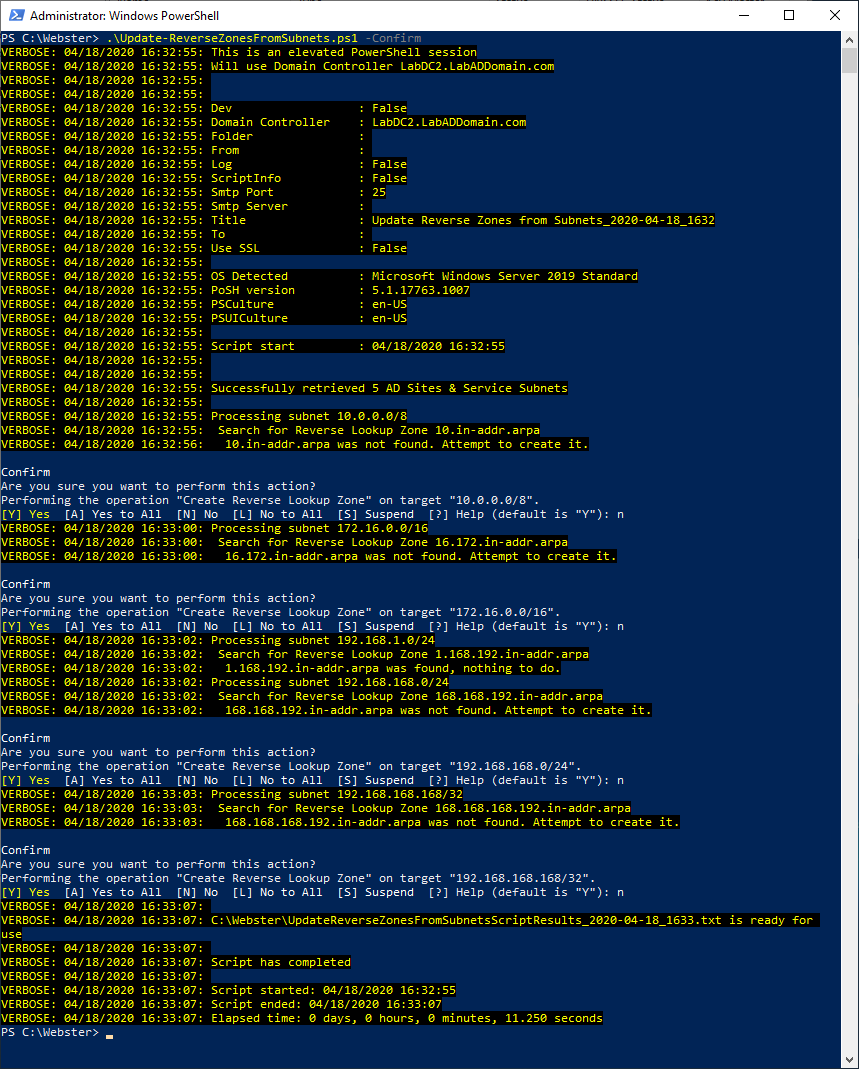
Figure 10 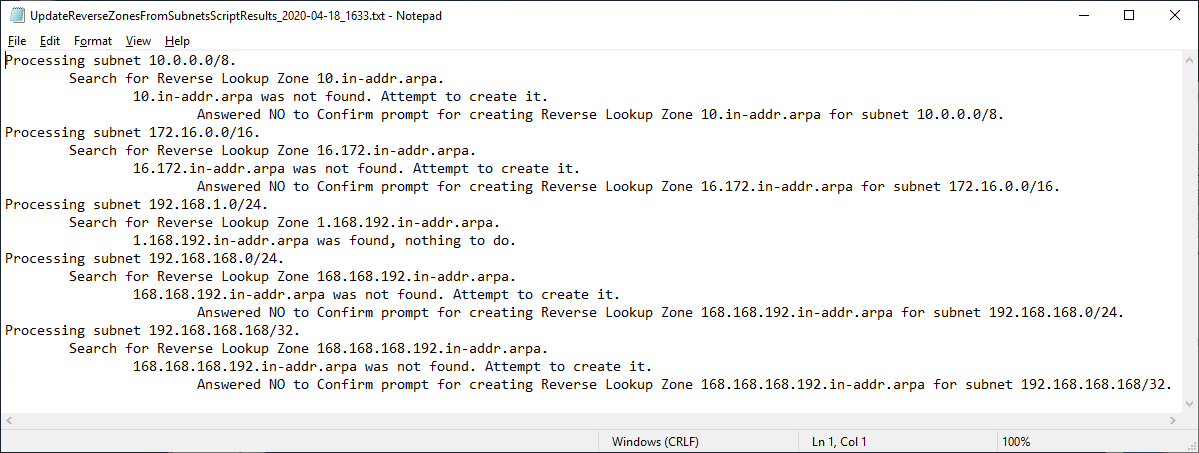
Figure 11 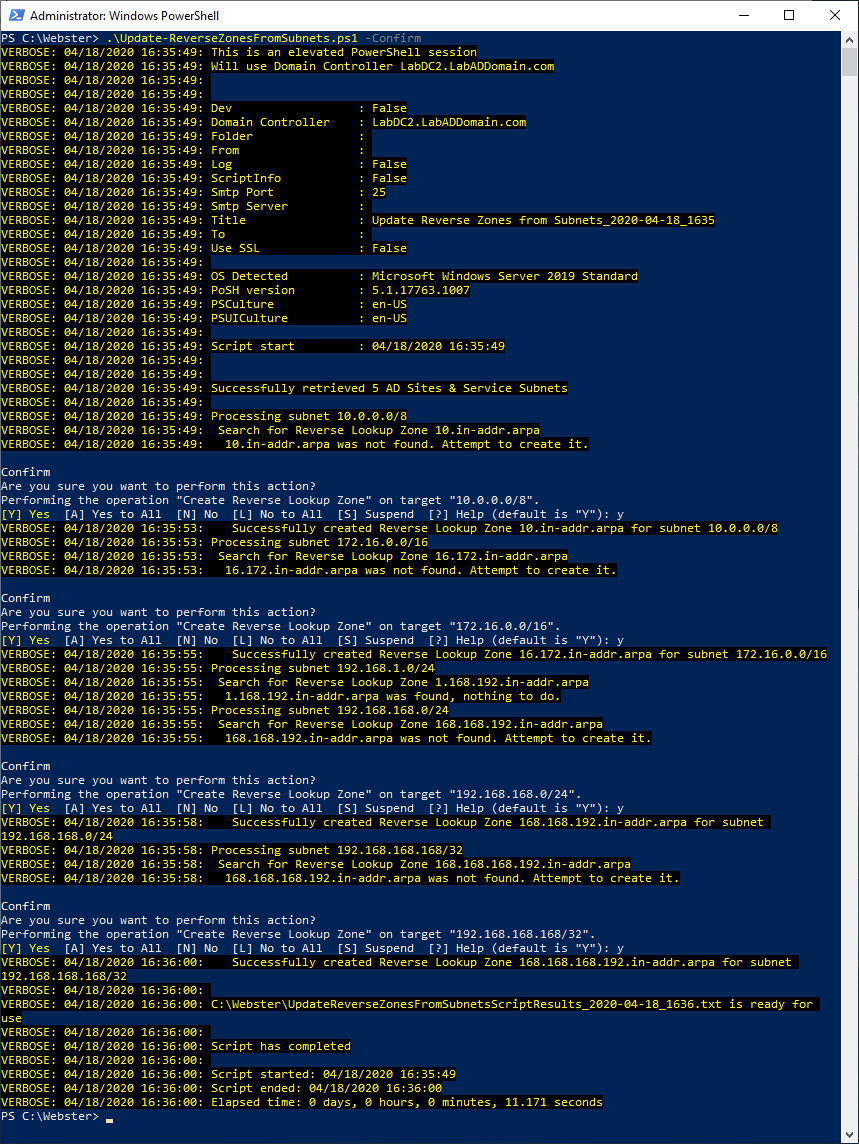
Figure 12 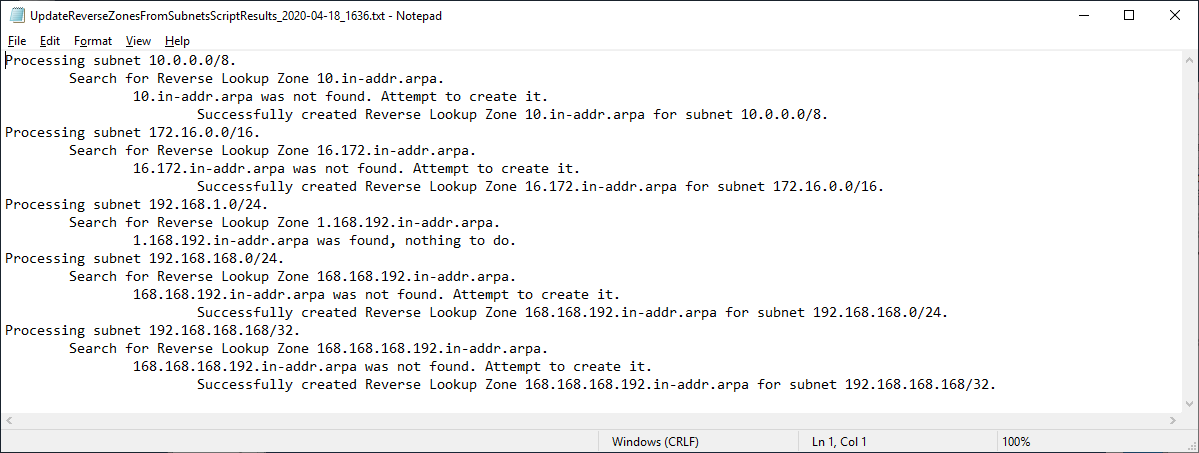
Figure 13 The main customer request for this script was to run it as a scheduled task and email the text file without saving the email credentials.
This requires using an unauthenticated email sent through an email relay server. This turned out to be simple to implement. I found the solution on ServerFault.
The solution was only three lines of PowerShell.
123$anonUsername = "anonymous"$anonPassword = ConvertTo-SecureString -String "anonymous" -AsPlainText -Force$anonCredentials = New-Object System.Management.Automation.PSCredential($anonUsername,$anonPassword)For on-premises Exchange, what the script requires to use an unauthenticated email is the From email account is “anonymous”. i.e. anonymous@emaildomain.tld.
The help text shows an example.
12345678910111213141516171819202122232425262728293031323334353637383940414243444546.EXAMPLEPS C:\PSScript > .\Get-SubnetsFromReverseZones.ps1-SmtpServer mailrelay.domain.tld-From Anonymous@domain.tld-To ITGroup@domain.tld***SENDING UNAUTHENTICATED EMAIL***The script will use the email server mailrelay.domain.tld, sending fromanonymous@domain.tld, sending to ITGroup@domain.tld.To send unauthenticated email using an email relay server requires the From email accountto use the name Anonymous.The script will use the default SMTP port 25 and will not use SSL.***GMAIL/G SUITE SMTP RELAY***To send email using a Gmail or g-suite account, you may have to turn ONthe "Less secure app access" option on your account.***GMAIL/G SUITE SMTP RELAY***The script will generate an anonymous secure password for the anonymous@domain.tldaccount..EXAMPLEPS C:\PSScript > .\Get-SubnetsFromReverseZones.ps1-SmtpServer labaddomain-com.mail.protection.outlook.com-UseSSL-From SomeEmailAddress@labaddomain.com-To ITGroupDL@labaddomain.com***OFFICE 365 Example***This uses Option 2 from the above link.***OFFICE 365 Example***The script will use the email server labaddomain-com.mail.protection.outlook.com, sending fromSomeEmailAddress@labaddomain.com, sending to ITGroupDL@labaddomain.com.The script will use the default SMTP port 25 and will use SSL.I tested this on the customer’s network and it worked the first time.
I have not tested the GMAIL/G Suite or Office 365 relay examples.
Adding the on-premises anonymous email capability required a change to a core script function (Function SendEmail), which means I will update every script using this function as soon as I can.
I want to again thank the customer for allowing me to give this script to the community and to all the testers.
If you find any issues with the script or any enhancement requests, send me an email.
I am creating the mirror image of this script to process reverse lookup zones and report (not create) on any missing subnets in Sites and Services.
You can always find the most current script by going to https://www.carlwebster.com/where-to-get-copies-of-the-documentation-scripts/
Thanks
Webster
2 Responses to “New Script: Update Active Directory DNS Reverse Lookup Zones from Sites and Services Subnets (Update-ReverseZonesFromSubnets.ps1)”






August 19, 2024 at 9:50 am
Carl, can this be modified to look at DHCP instead of Sites and Services? Thanks.
August 20, 2024 at 4:48 am
What does DHCP have to do with DNS Reverse Lookup Zones?
This script was created based on my recommendations for conducting hundreds of AD audits and remediations. Having DNS reverse lookup Zones is important for most SBC and VDI products. Not everyone uses Microsoft DHCP, but everyone using AD uses AD Sites and Services. Of course, this script is useless if you are using something other than Microsoft DNS.
Thanks
Webster