-
Inside Webster’s Lab: Creating Active Directory Organizational Units, Users, Groups and Computers Using PowerShell
January 1, 2015
OK, I heard from enough of you that wanted me to do this in PowerShell instead of my batch file. Here is the original article using built-in Windows utilities. This article will show the original batch file converted to PowerShell.
I created four variables. One for the domain name, one for the top-level domain identifier, one to determine if you want the OUs protected from accidental deletion, and the last to hold the initial password as a secure string.
The structure of the script is the same as the original batch file:
- Creates the OUs
- Creates the security groups
- Creates the user accounts
- Adds the user accounts into the security groups
- Creates the computer accounts
123456789101112131415161718192021222324252627282930313233343536373839404142434445464748495051525354555657585960616263646566676869707172737475767778798081828384858687888990919293949596979899100101102103104105106107108109110111112113114115116117118119120121122123124$ADDomain= "labaddomain"$TLD= "com"$Protect=$False$CryptoPwd= (ConvertTo-SecureString-AsPlainText"FakePwd"-Force)#Create OUsNew-ADOrganizationalUnit-Name"Lab" `-Path"dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Accounts" `-Path"ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Admin" `-Path"ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Service" `-Path"ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"User" `-Path"ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Desktops" `-Path"ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Admin" `-Path"ou=Desktops,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"XD76" `-Path"ou=Desktops,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Groups" `-Path"ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Admin" `-Path"ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Desktops" `-Path"ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"User" `-Path"ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"Servers" `-Path"ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"PVS" `-Path"ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verboseNew-ADOrganizationalUnit-Name"XD76" `-Path"ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion$Protect-verbose#Create AD security groupsNew-ADGroup-Name"LocalAdmins"-SamAccountNameLocalAdmins `-GroupCategorySecurity-GroupScopeGlobal `-DisplayName"Groupforusers who need local admin rights" `-Path"ou=Admin,ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-Description"Groupforusers who need local admin rights"-verboseNew-ADGroup-Name"XDUsers"-SamAccountNameXDUsers `-GroupCategorySecurity-GroupScopeGlobal `-DisplayName"Groupforusers who need XenDesktop desktop access" `-Path"ou=User,ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-Description"Groupforusers who need XenDesktop desktop access"-verbose#Create user accountsNew-ADUser-Namesvc_ctxpvs-AccountPassword$CryptoPwd`-CannotChangePassword$True-ChangePasswordAtLogon$False`-Description"Citrix PVS Service Account" `-DisplayName"Citrix PVS Service Account"-Enabled$True`-PasswordNeverExpires$True`–Path "ou=Service,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName"svc_ctxpvs" –UserPrincipalName "svc_ctxpvs@$ADDomain.$TLD" `-verboseNew-ADUser-Namesvc_ctxsqldb-AccountPassword$CryptoPwd`-CannotChangePassword$True-ChangePasswordAtLogon$False`-Description"Citrix SQL DBA Service Account" `-DisplayName"Citrix SQL DBA Service Account"-Enabled$True`-PasswordNeverExpires$True`–Path "ou=Service,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName"svc_ctxsqldb" –UserPrincipalName "svc_ctxsqldb@$ADDomain.$TLD" `-verboseNew-ADUser-NameUser1-AccountPassword$CryptoPwd`-CannotChangePassword$True-ChangePasswordAtLogon$False`-Description"User1 PvD" `-DisplayName"User1"-Enabled$True`-PasswordNeverExpires$True`–Path "ou=User,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName"User1" –UserPrincipalName "User1@$ADDomain.$TLD" `-verboseNew-ADUser-NameUser2-AccountPassword$CryptoPwd`-CannotChangePassword$True-ChangePasswordAtLogon$False`-Description"User2 PvD" `-DisplayName"User2"-Enabled$True`-PasswordNeverExpires$True`–Path "ou=User,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName"User2" –UserPrincipalName "User2@$ADDomain.$TLD" `-verboseNew-ADUser-NameUser3-AccountPassword$CryptoPwd`-CannotChangePassword$True-ChangePasswordAtLogon$False`-Description"User3 PvD" `-DisplayName"User3"-Enabled$True`-PasswordNeverExpires$True`–Path "ou=User,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName"User3" –UserPrincipalName "User3@$ADDomain.$TLD" `-verbose#all users in the Lab/Accounts/User OU get added to the XDUsers security group$Users=get-aduser`-searchbase"ou=user,ou=accounts,ou=lab,dc=$ADDomain,dc=$tld" `-filter*Add-ADGroupMember-IdentityXDUsers-Members$Users#any user in the Lab/Accounts/User OU that has PvD in the description#gets added to the LocalAdmins security group$Users=get-aduser`-searchbase"ou=user,ou=accounts,ou=lab,dc=$ADDomain,dc=$tld" `-filter'Description -like "*PvD*"'Add-ADGroupMember-IdentityLocalAdmins-Members$Users#Create AD computer accountsNew-ADComputer-NamePVS76-SamAccountNamePVS76-Description"PVS76" `-Path"ou=PVS,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD"-Enabled$True-verboseNew-ADComputer-NameXD76-SamAccountNameXD76-Description"XD76" `-Path"ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD"-Enabled$True-verboseNew-ADComputer-NameDirector-SamAccountNameDirector-Description"Director" `-Path"ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD"-Enabled$True-verboseNew-ADComputer-NameStoreFront-SamAccountNameStoreFront-Description"StoreFront" `-Path"ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD"-Enabled$True-verboseNew-ADComputer-NameSQL-SamAccountNameSQL-Description"SQL" `-Path"ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD"-Enabled$True-verboseI named the script CreateLab.ps1.
Figure 1 shows my Active Directory structure before running the script.
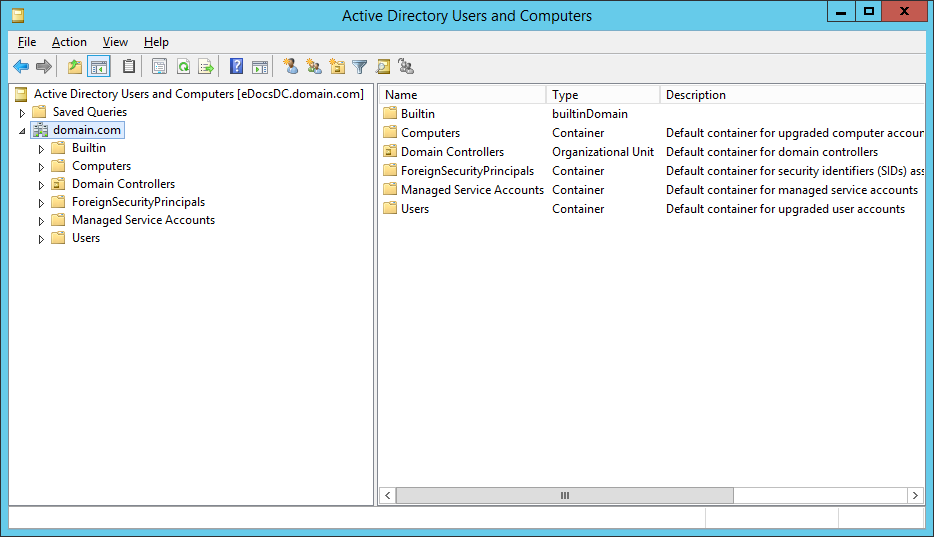
Figure 1 Figure 2 shows the results of running the PowerShell script.
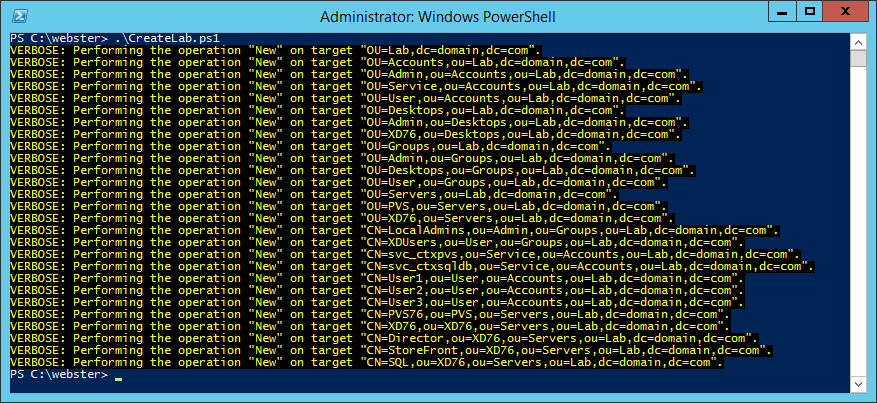
Figure 2 Figures 3 through 13 show the AD structure after running the script (which matches running the batch file).
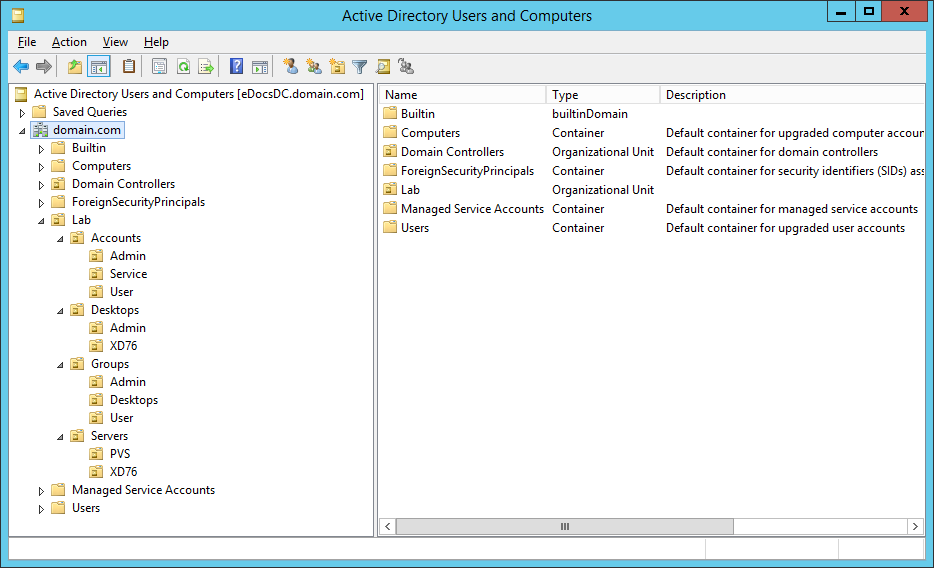
Figure 3 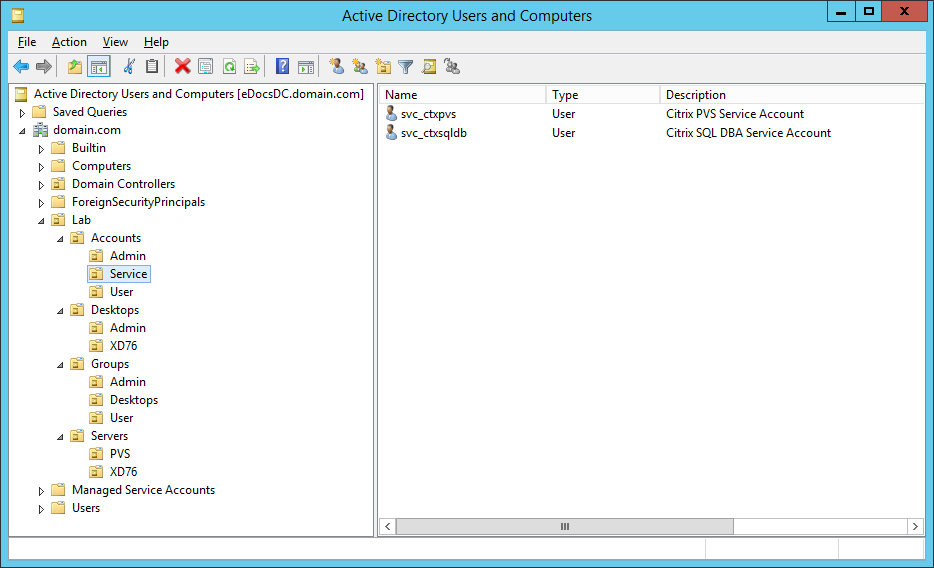
Figure 4 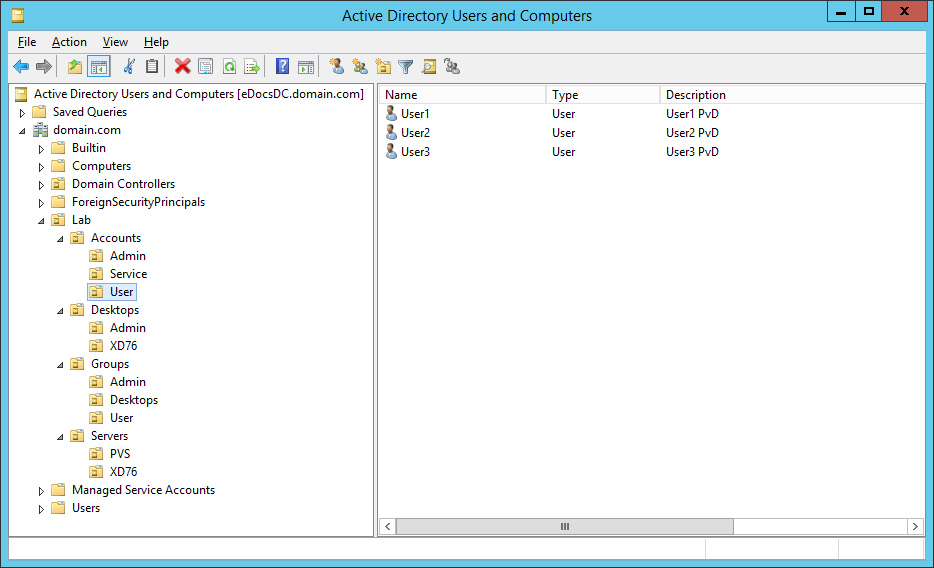
Figure 5 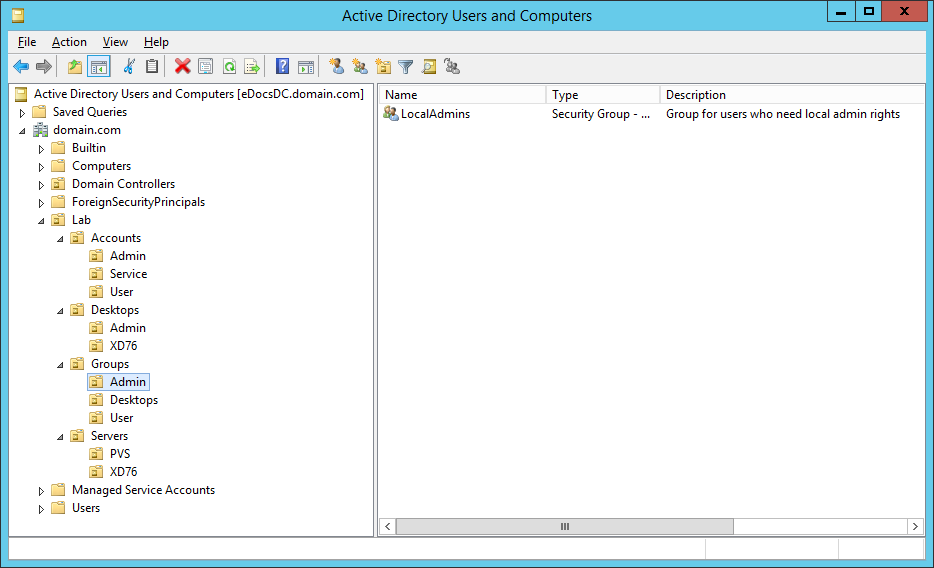
Figure 6 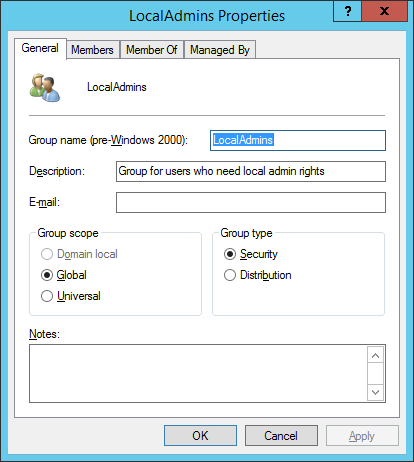
Figure 7 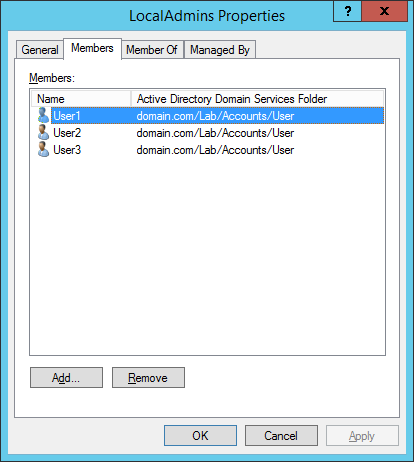
Figure 8 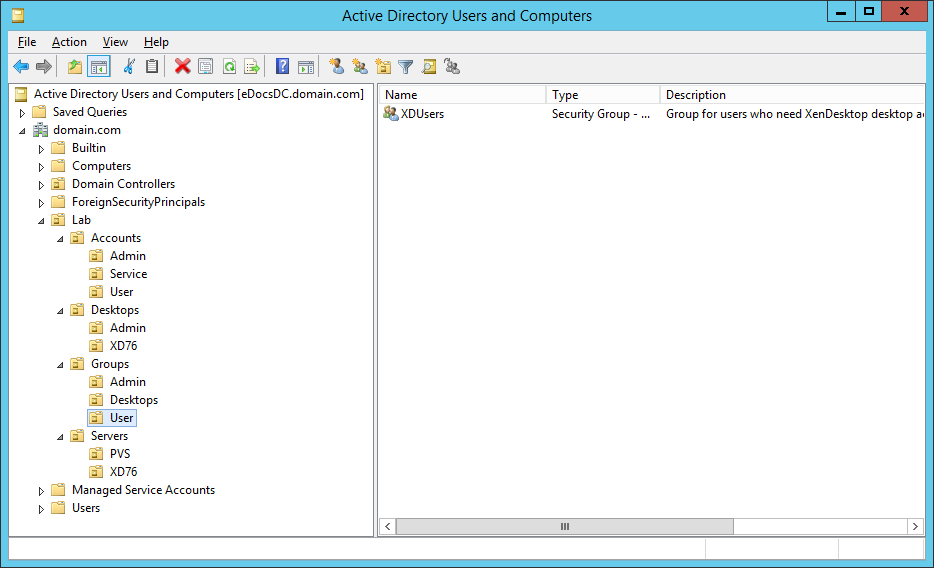
Figure 9 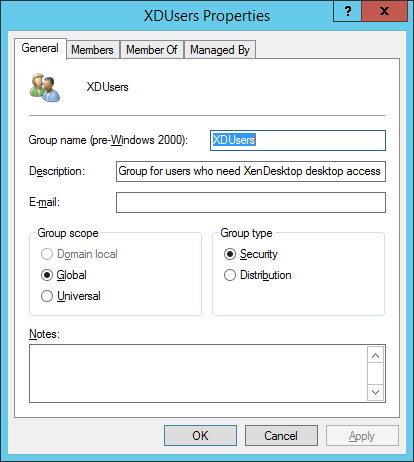
Figure 10 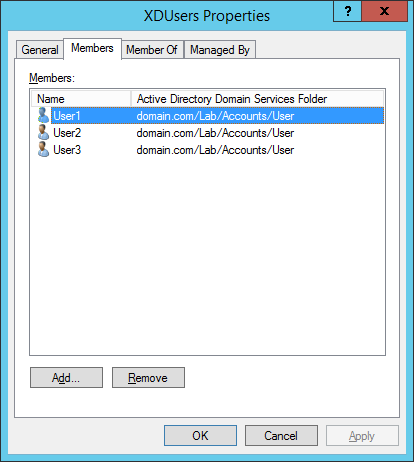
Figure 11 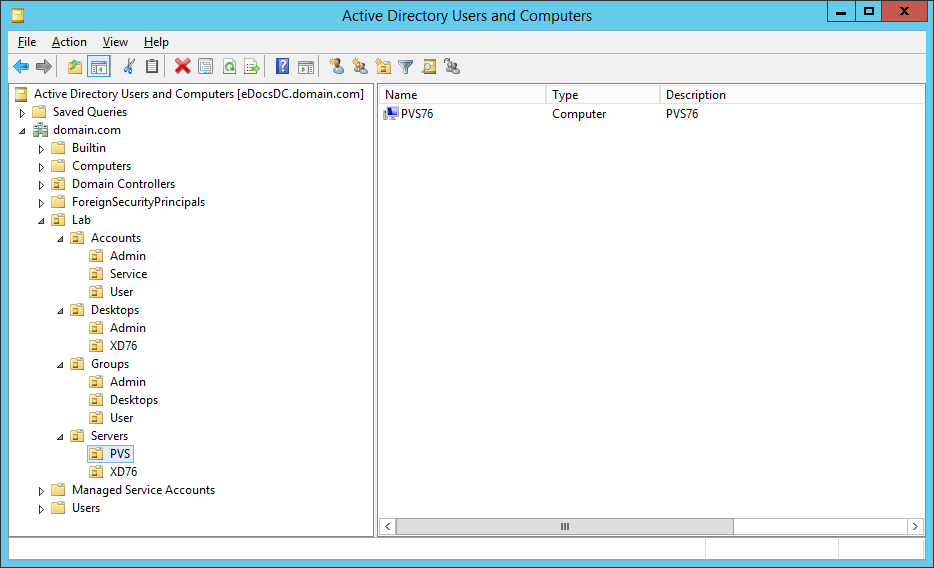
Figure 12 
Figure 13 There you go, a PowerShell version of the batch file I use to create my lab’s AD structure.
You can get a PS1 version here and a TXT version here.
Thanks
Webster
2 Responses to “Inside Webster’s Lab: Creating Active Directory Organizational Units, Users, Groups and Computers Using PowerShell”






January 7, 2015 at 9:39 pm
Carl,
I didn’t mean for you to burn your free time to convert the batch file to PS!!! Cool that you provided the PS script to accomplish the same as the batch file. I intend to test this sucker out.
Thanks for providiing your knowledge…always a great resource.
Rob
January 8, 2015 at 7:34 am
Only took an hour to do it.
Webster