-
Inside Webster’s Lab: Creating Active Directory Organizational Units, Users, Groups and Computers
December 31, 2014
With all the writing I do for my website and customers, I recreate my Windows Server 2012 R2 Active Directory (AD) environment frequently. I thought I would show you how, in just a few seconds, I recreate my entire AD structure.
This may come as a shock to some of you but I do not use PowerShell for this task. Instead, I use built-in Windows utilities that I have been using since probably around 2004. What I use works, so I see no need to redo it in PowerShell. I only use three Windows utilities:
- DSAdd
- DSMod
- DSQuery
I have a batch file that does the following:
- Creates the OUs
- Creates the security groups
- Creates the user accounts
- Adds the user accounts into the security groups
- Creates the computer accounts
I pre-create all the computer accounts so when the computers are joined to the domain, they are in the right OU and get the necessary GPOs immediately after the domain join restart.
The batch file is very simple (to me).
Note: The batch file contains several “-upn something@domain.com”. These seem to confuse the syntax highlighter I use for WordPress. The highlighter treated everything after the “something@domain.com” as JavaScript and really scrambled the rest of the text. Just in the text below, I changed all the “something@domain.com” to “something at domain.com” just for this article but they are still there in the batch file you can download.
1234567891011121314151617181920212223242526272829303132333435363738394041424344454647484950515253echo offCLSEcho Create OUsDsadd ou "ou=Lab,dc=LabADDomain,dc=com" -desc "top level OU for Lab"Dsadd ou "ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -desc "Accounts top level OU"Dsadd ou "ou=Admin,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for Admin accounts"Dsadd ou "ou=Service,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for service accounts"Dsadd ou "ou=User,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for regular user account"Dsadd ou "ou=Desktops,ou=Lab,dc=LabADDomain,dc=com" -desc "Desktops top level OU"Dsadd ou "ou=Admin,ou=Desktops,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for administrator desktops"Dsadd ou "ou=XD76,ou=Desktops,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for regular user desktops"Dsadd ou "ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -desc "Security Groups top level OU"Dsadd ou "ou=Admin,ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for admin security groups"Dsadd ou "ou=Desktops,ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for desktop computer security groups"Dsadd ou "ou=User,ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for regular user security groups"Dsadd ou "ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -desc "Servers top level OU"Dsadd ou "ou=PVS,ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for PVS servers"Dsadd ou "ou=XD76,ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -desc "OU for all other XenDesktop servers"Echo Create security groupsDsadd group "cn=LocalAdmins,ou=Admin,ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -secgrp yes -desc "Group for users who need local admin rights"Dsadd group "cn=XDUsers,ou=User,ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -secgrp yes -desc "Group for users who need XenDesktop desktop access"Echo Create user accountsDsadd user "cn=svc_ctxpvs,ou=Service,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -samid svc_ctxpvs -upn svc_ctxpvs at LabADDomain.com -fn svc_ctxpvs -display "svc_ctxpvs" -pwd FakePwd -desc "Citrix PVS Service Account" -mustchpwd no -pwdneverexpires yesDsadd user "cn=svc_ctxsqldb,ou=Service,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -samid svc_ctxsqldb -upn svc_ctxsqldb at LabADDomain.com -fn svc_ctxsqldb -display "svc_ctxsqldb" -pwd FakePwd -desc "Citrix SQL DBA Service Account" -mustchpwd no -pwdneverexpires yesDsadd user "cn=User1,ou=User,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -samid User1 -upn User1 at LabADDomain.com -fn User1 -display "User1" -pwd FakePwd -desc "User1 PvD" -mustchpwd no -pwdneverexpires yesDsadd user "cn=User2,ou=User,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -samid User2 -upn User2 at LabADDomain.com -fn User2 -display "User2" -pwd FakePwd -desc "User2 PvD" -mustchpwd no -pwdneverexpires yesDsadd user "cn=User3,ou=User,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -samid User3 -upn User3 at LabADDomain.com -fn User3 -display "User3" -pwd FakePwd -desc "User3 PvD" -mustchpwd no -pwdneverexpires yesEcho Add user accounts to security groupsRem all users in the Lab/Accounts/User OU get added to the XDUsers security groupdsquery user "ou=User,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -limit 0 | dsmod group "cn=XDUsers,ou=User,ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -chmbr -cRem any user in the Lab/Accounts/User OU that has PvD in the description gets added to the LocalAdmins security groupdsquery user "ou=User,ou=Accounts,ou=Lab,dc=LabADDomain,dc=com" -desc "*PvD*" -limit 0 | dsmod group "cn=LocalAdmins,ou=Admin,ou=Groups,ou=Lab,dc=LabADDomain,dc=com" -chmbr -cEcho Create computer accountsDsadd computer "cn=PVS76,ou=PVS,ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -samid PVS76 -desc "PVS76"Dsadd computer "cn=XD76,ou=XD76,ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -samid XD76 -desc "XD76"Dsadd computer "cn=Director,ou=XD76,ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -samid Director -desc "Director"Dsadd computer "cn=StoreFront,ou=XD76,ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -samid StoreFront -desc "StoreFront"Dsadd computer "cn=SQL,ou=XD76,ou=Servers,ou=Lab,dc=LabADDomain,dc=com" -samid SQL -desc "SQL"echo onThe results of running the batch file.
Note: In the text below, I also had to change all the “something@domain.com” to “something at domain.com” just for this article but they are still there in the batch file you can download.
1234567891011121314151617181920212223242526272829303132333435363738394041424344454647484950515253545556575859606162636465666768697071Echo Create OUsCreate OUsDsadd ou "ou=Lab,dc=labaddomain,dc=com" -desc "top level OU for Lab"dsadd succeeded:ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -desc "Accounts top level OU"dsadd succeeded:ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Admin,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -desc "OU for Admin accounts"dsadd succeeded:ou=Admin,ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Service,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -desc "OU for service accounts"dsadd succeeded:ou=Service,ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -desc "OU for regular user account"dsadd succeeded:ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Desktops,ou=Lab,dc=labaddomain,dc=com" -desc "Desktops top level OU"dsadd succeeded:ou=Desktops,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Admin,ou=Desktops,ou=Lab,dc=labaddomain,dc=com" -desc "OU for administrator desktops"dsadd succeeded:ou=Admin,ou=Desktops,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=XD76,ou=Desktops,ou=Lab,dc=labaddomain,dc=com" -desc "OU for regular user desktops"dsadd succeeded:ou=XD76,ou=Desktops,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Groups,ou=Lab,dc=labaddomain,dc=com" -desc "Security Groups top level OU"dsadd succeeded:ou=Groups,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Admin,ou=Groups,ou=Lab,dc=labaddomain,dc=com" -desc "OU for admin security groups"dsadd succeeded:ou=Admin,ou=Groups,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Desktops,ou=Groups,ou=Lab,dc=labaddomain,dc=com" -desc "OU for desktop computer security groups"dsadd succeeded:ou=Desktops,ou=Groups,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=User,ou=Groups,ou=Lab,dc=labaddomain,dc=com" -desc "OU for regular user security groups"dsadd succeeded:ou=User,ou=Groups,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=Servers,ou=Lab,dc=labaddomain,dc=com" -desc "Servers top level OU"dsadd succeeded:ou=Servers,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=PVS,ou=Servers,ou=Lab,dc=labaddomain,dc=com" -desc "OU for PVS servers"dsadd succeeded:ou=PVS,ou=Servers,ou=Lab,dc=labaddomain,dc=comDsadd ou "ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=com" -desc "OU for all other XenDesktop servers"dsadd succeeded:ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=comEcho Create security groupsCreate security groupsDsadd group "cn=LocalAdmins,ou=Admin,ou=Groups,ou=Lab,dc=labaddomain,dc=com" -secgrp yes -desc "Group for users who need local admin rights"dsadd succeeded:cn=LocalAdmins,ou=Admin,ou=Groups,ou=Lab,dc=labaddomain,dc=comDsadd group "cn=XDUsers,ou=User,ou=Groups,ou=Lab,dc=labaddomain,dc=com" -secgrp yes -desc "Group for users who need XenDesktop desktop access"dsadd succeeded:cn=XDUsers,ou=User,ou=Groups,ou=Lab,dc=labaddomain,dc=comEcho Create user accountsCreate user accountsDsadd user "cn=svc_ctxpvs,ou=Service,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -samid svc_ctxpvs -upn svc_ctxpvs at labaddomain -fn svc_ctxpvs -display "svc_ctxpvs" -pwd FakePwd -desc "Citrix PVS Service Account" -mustchpwd no -pwdneverexpires yesdsadd succeeded:cn=svc_ctxpvs,ou=Service,ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd user "cn=svc_ctxsqldb,ou=Service,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -samid svc_ctxsqldb -upn svc_ctxsqldb at labaddomain -fn svc_ctxsqldb -display "svc_ctxsqldb" -pwd FakePwd -desc "Citrix SQL DBA Service Account" -mustchpwd no -pwdneverexpires yesdsadd succeeded:cn=svc_ctxsqldb,ou=Service,ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd user "cn=User1,ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -samid User1 -upn User1 at labaddomain -fn User1 -display "User1" -pwd FakePwd -desc "User1 PvD" -mustchpwd no -pwdneverexpires yesdsadd succeeded:cn=User1,ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd user "cn=User2,ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -samid User2 -upn User2 at labaddomain -fn User2 -display "User2" -pwd FakePwd -desc "User2 PvD" -mustchpwd no -pwdneverexpires yesdsadd succeeded:cn=User2,ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=comDsadd user "cn=User3,ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -samid User3 -upn User3 at labaddomain -fn User3 -display "User3" -pwd FakePwd -desc "User3 PvD" -mustchpwd no -pwdneverexpires yesdsadd succeeded:cn=User3,ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=comEcho Add user accounts to security groupsAdd user accounts to security groupsRem all users in the Lab/Accounts/User OU get added to the XDUsers security groupdsquery user "ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -limit 0 | dsmod group "cn=XDUsers,ou=User,ou=Groups,ou=Lab,dc=labaddomain,dc=com" -chmbr -cdsmod succeeded:cn=XDUsers,ou=User,ou=Groups,ou=Lab,dc=labaddomain,dc=comRem any user in the Lab/Accounts/User OU that has PvD in the description gets added to the LocalAdmins security groupdsquery user "ou=User,ou=Accounts,ou=Lab,dc=labaddomain,dc=com" -desc "*PvD*" -limit 0 | dsmod group "cn=LocalAdmins,ou=Admin,ou=Groups,ou=Lab,dc=labaddomain,dc=com" -chmbr -cdsmod succeeded:cn=LocalAdmins,ou=Admin,ou=Groups,ou=Lab,dc=labaddomain,dc=comEcho Create computer accountsCreate computer accountsDsadd computer "cn=PVS76,ou=PVS,ou=Servers,ou=Lab,dc=labaddomain,dc=com" -samid PVS76 -desc "PVS76"dsadd succeeded:cn=PVS76,ou=PVS,ou=Servers,ou=Lab,dc=labaddomain,dc=comDsadd computer "cn=XD76,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=com" -samid XD76 -desc "XD76"dsadd succeeded:cn=XD76,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=comDsadd computer "cn=Director,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=com" -samid Director -desc "Director"dsadd succeeded:cn=Director,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=comDsadd computer "cn=StoreFront,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=com" -samid StoreFront -desc "StoreFront"dsadd succeeded:cn=StoreFront,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=comDsadd computer "cn=SQL,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=com" -samid SQL -desc "SQL"dsadd succeeded:cn=SQL,ou=XD76,ou=Servers,ou=Lab,dc=labaddomain,dc=comecho onC:\>And the results in AD.
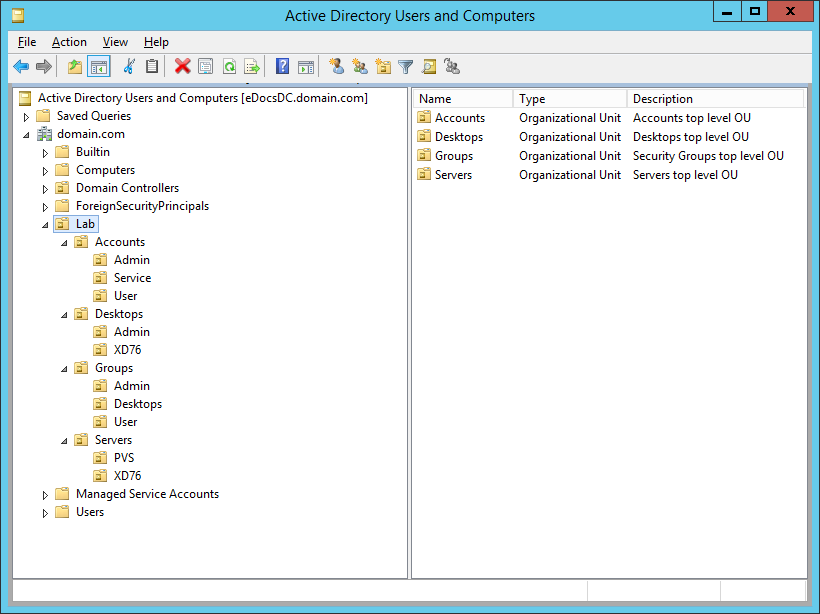
Figure 1 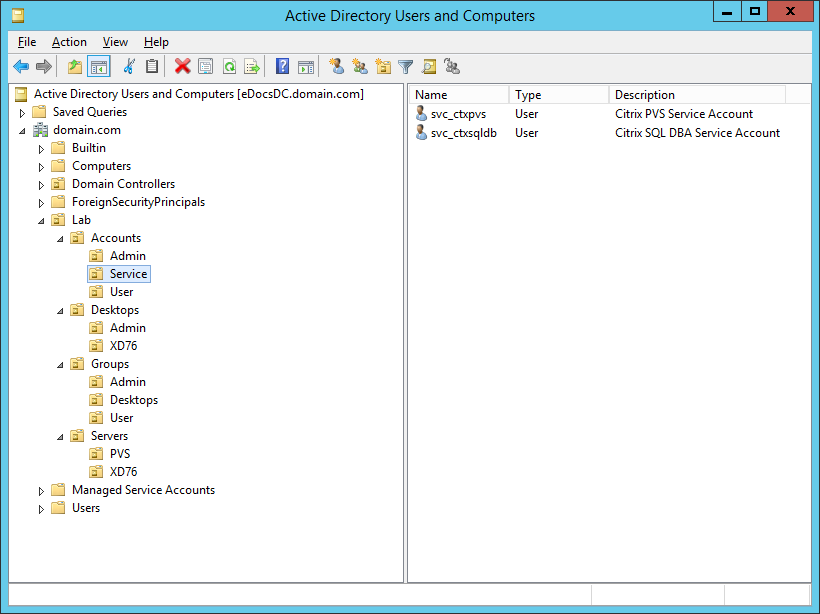
Figure 2 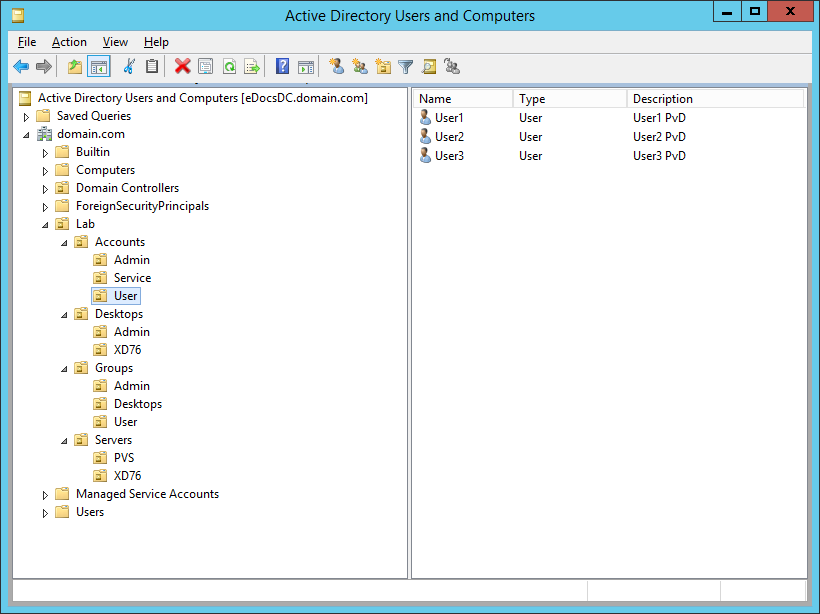
Figure 3 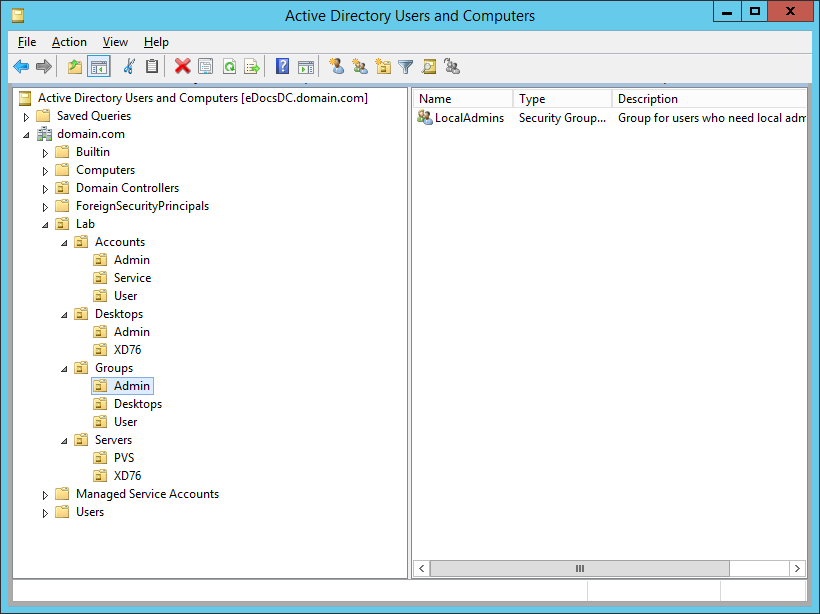
Figure 4 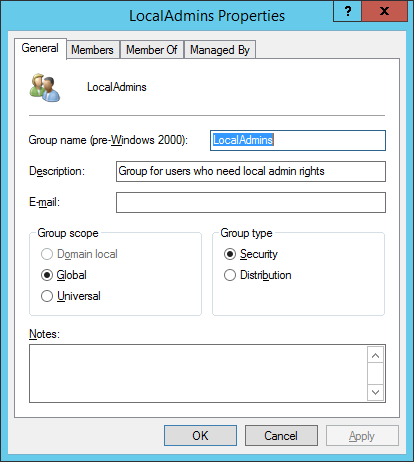
Figure 5 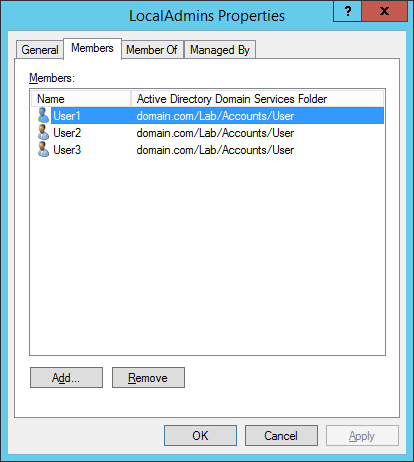
Figure 6 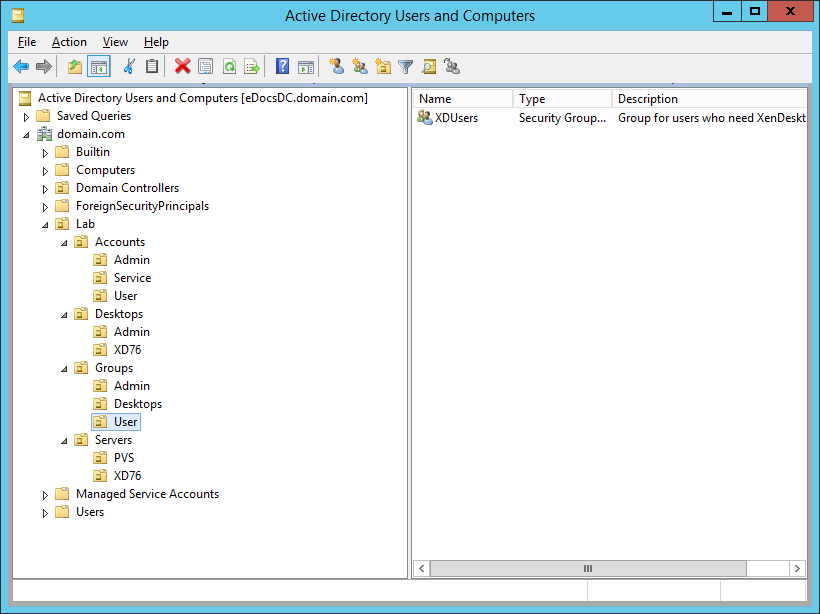
Figure 7 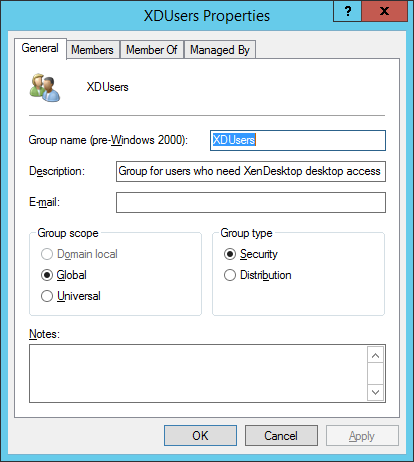
Figure 8 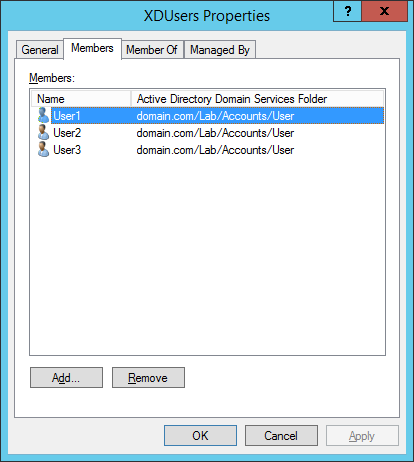
Figure 9 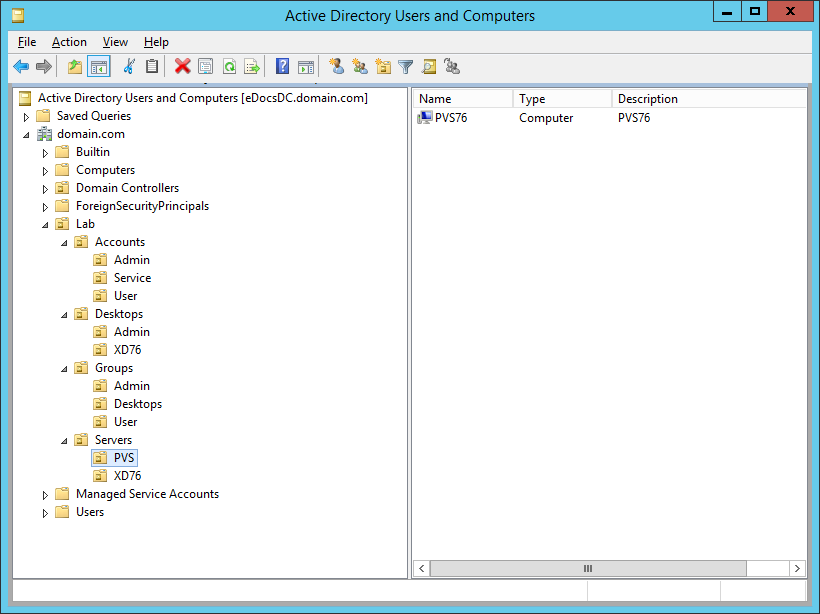
Figure 10 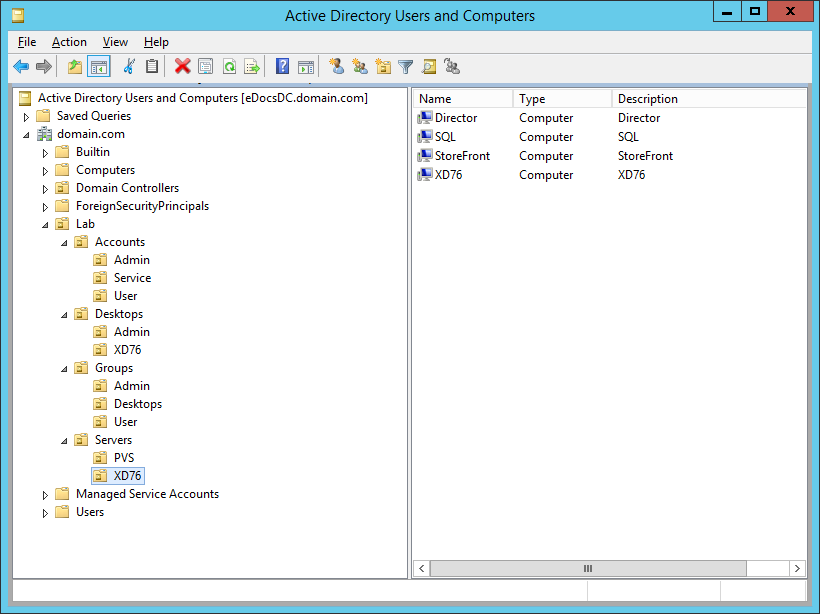
Figure 11 And there you have the very quick and very simple way I can create and recreate my AD lab structure. To delete the structure, I just right-click the top-level Lab OU and select delete as shown in Figure 12.
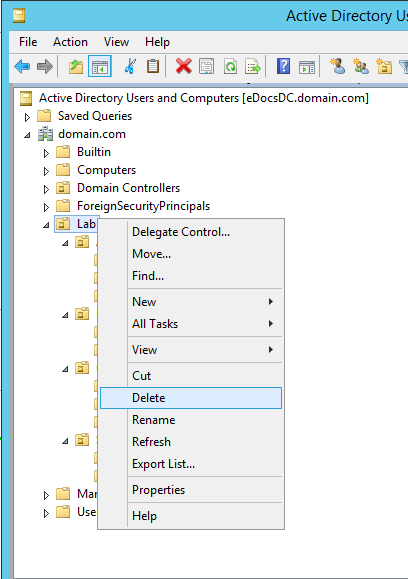
Figure 12 Click Yes to the popup shown in Figure 13.
Figure 13 Select Use Delete Subtree server control and click Yes as shown in Figure 14.
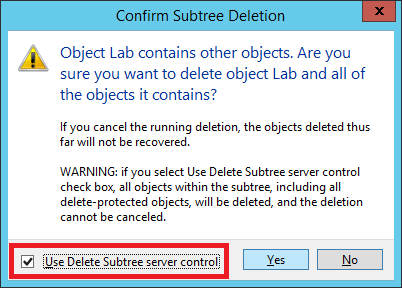
Figure 14 And in less than the blink of an eye, the Lab OU structure is removed from AD as shown in Figure 15.
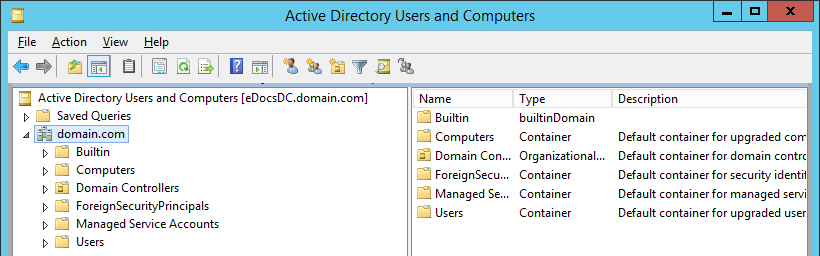
Figure 15 Since DSAdd OU does not have a parameter to set the Protect this OU from accidental deletion flag, it is very simple to delete the Lab OU tree and run the batch file to recreate the Lab OU structure whenever I need to have a clean (re)starting point.
I hope this very quick and simple process helps you out.
Thanks
Webster
3 Responses to “Inside Webster’s Lab: Creating Active Directory Organizational Units, Users, Groups and Computers”






January 1, 2015 at 8:37 am
That is a nice little batch script!!! I just have to ask…have you thought about converting it to PS? Thanks for posting…I always find your information very valuable. Keep up the good work.
Rob
January 1, 2015 at 9:03 am
Why? The batch file is simple, uses built-in utilities and works fine.
But it would be very easy, I think, to convert it to PowerShell.
Webster
January 1, 2015 at 11:27 am
Here you go.
https://www.carlwebster.com/inside-websters-lab-creating-active-directory-organizational-units-users-groups-computers-using-powershell/
Webster