-
Creating a Group Policy using Microsoft PowerShell to Configure the Authoritative Time Server
August 8, 2013
In my 10 Things in AD… presentations, I talk about the importance of having the domain controller that holds the Primary Domain Controller Emulator (PDCe) role configured as the authoritative time source for the forest. In the PDF that accompanies the presentations, I include a link to a Microsoft Ask the Directory Service Team blog article. The main problem with that article is there is not enough detail for a lot of people. Now that Server 2008 and later include PowerShell cmdlets for Group Policy, I thought I would add some detail on creating the Group Policy with PowerShell.
There is no way to use the in-the-box Group Policy PowerShell cmdlets to create WMI Filters. For that, there is a Group Policy WMI filter cmdlet module available. I downloaded the module and placed it in my scripts folder, c:\webster. There was an issue for me and I had to change one line in the module.
I had to change line 70 from:
$msWMIAuthor = (Get-ADUser $env:USERNAME).UserPrincipalName
To:
$msWMIAuthor = (Get-ADUser $env:USERNAME).Name
Without that change, I received an error on line 97 with a Null value in the $Attr array defined in line 80. I traced the Null value to the msWMI-Author value in the array.
The script to create the Group Policy:
Set-StrictMode -Version 2 #Carl Webster, CTP and independent consultant #webster@carlwebster.com #@carlwebster on Twitter #https://www.carlwebster.com #With help from Michael B. Smith - <a href="https://www.essential.exchange/blog/" target="_blank" rel="noopener">https://www.essential.exchange/blog/</a> # load required modules Import-Module ActiveDirectory Import-Module GroupPolicy #the following module is available for download from #http://gallery.technet.microsoft.com/scriptcenter/Group-Policy-WMI-filter-38a188f3 #assuming the module is in the same folder as the script Import-Module ( Join-Path ( Split-Path $MyInvocation.MyCommand.Path -Parent) GPWmiFilter.psm1 ) #define variables specific to an AD environment $GPOName = 'Set PDCe as Authoritative Time Server' $defaultNC = ( [ADSI]"LDAP://RootDSE" ).defaultNamingContext.Value $TargetOU = 'OU=Domain Controllers,' + $defaultNC $TimeServer = 'north-america.pool.ntp.org,0x1' $WMIFilterName = 'PDCe Role Filter' #the GPWmiFilter module said to put this in the main code new-itemproperty "HKLM:\System\CurrentControlSet\Services\NTDS\Parameters" ` -name "Allow System Only Change" -value 1 -propertyType dword -EA 0 #create WMI Filter $filter = New-GPWmiFilter -Name $WMIFilterName ` -Expression 'Select * from Win32_ComputerSystem where DomainRole = 5' ` -Description 'Queries for the Domain Controller that holds the PDCe FSMO Role' ` -PassThru #create new GPO shell $GPO = New-GPO -Name $GPOName #add WMI filter $GPO.WmiFilter = $Filter #set the three registry keys in the Preferences section of the new GPO Set-GPPrefRegistryValue -Name $GPOName -Action Update -Context Computer ` -Key 'HKLM\SYSTEM\CurrentControlSet\Services\W32Time\Config' ` -Type DWord -ValueName 'AnnounceFlags' -Value 5 | out-null Set-GPPrefRegistryValue -Name $GPOName -Action Update -Context Computer ` -Key 'HKLM\SYSTEM\CurrentControlSet\Services\W32Time\Parameters' ` -Type String -ValueName 'NtpServer' -Value $TimeServer | out-null Set-GPPrefRegistryValue -Name $GPOName -Action Update -Context Computer ` -Key 'HKLM\SYSTEM\CurrentControlSet\Services\W32Time\Parameters' ` -Type String -ValueName 'Type' -Value 'NTP' | out-null #link the new GPO to the Domain Controllers OU New-GPLink -Name $GPOName ` -Target $TargetOU | out-null
My Group Policy Management Console (GPMC) before running the script is shown in Figure 1 showing no WMI Filters exist.
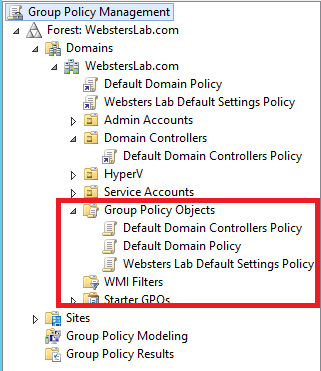
Figure 1 The script is processed and then I ran the Get-GPO cmdlet to verify the GPO was created (Figure 2).
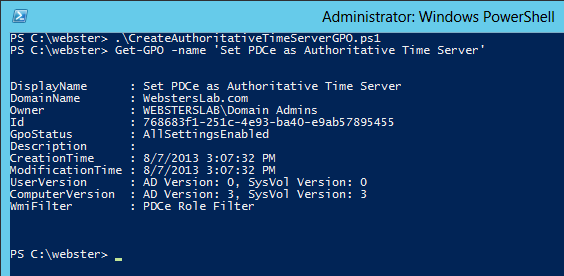
Figure 2 After a refresh, a look back in the GPMC (Figure 3) showing the new WMI Filter and GPO.
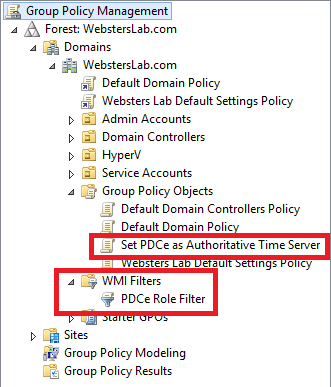
Figure 3 Selecting the new WMI Filter in the GPMC shows all the settings are correct: Filter Name, Description, and Query as shown in Figure 4.
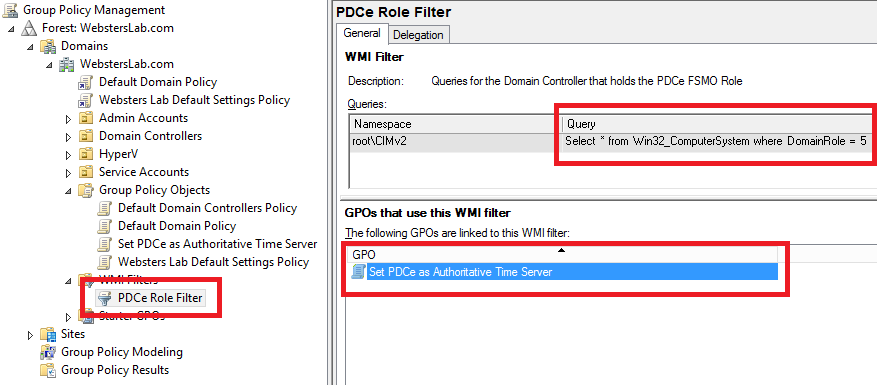
Figure 4 Another look in the GPMC at the Domain Controllers OU shows the new GPO is linked properly as shown in Figure 5.
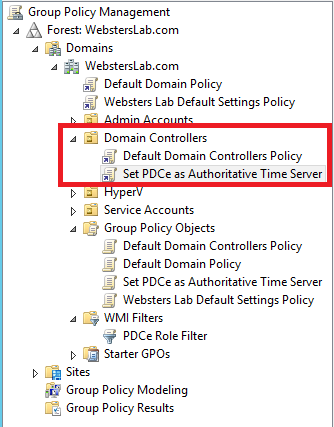
Figure 5 And Figure 6 shows all the registry keys are set properly.
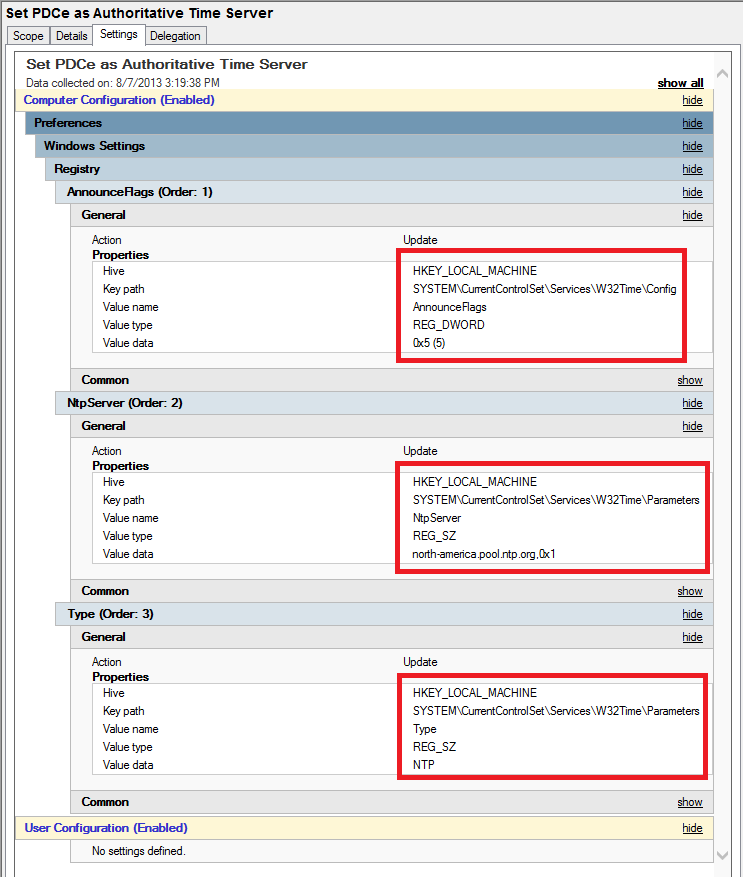
Figure 6 The current registry keys are shown in Figures 7 and 8.
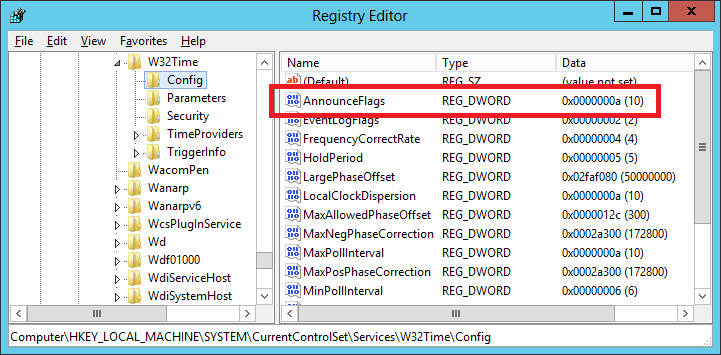
Figure 7 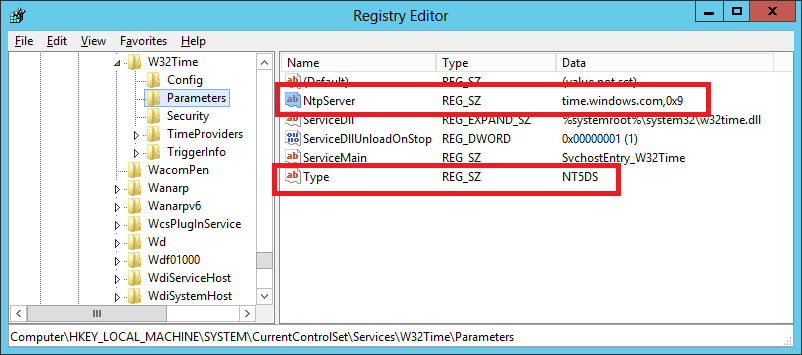
Figure 8 After a GPUPDATE /FORCE, the registry keys are shown in Figures 9 and 10.
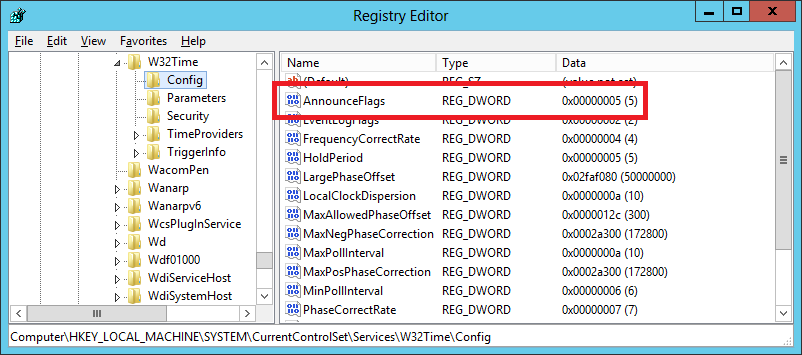
Figure 9 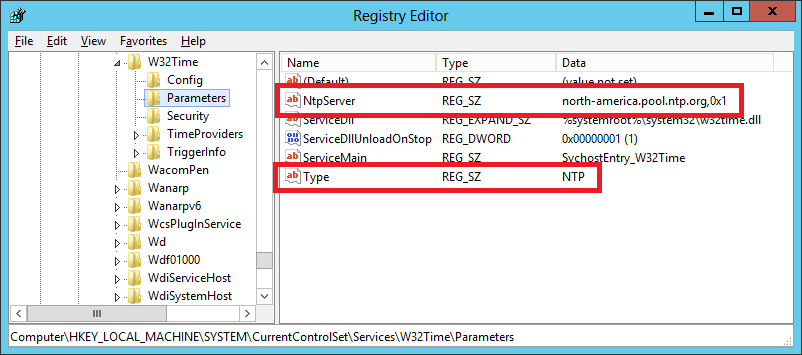
Figure 10 What happens on a domain controller that is not the PDCe? That is shown in Figure 11. As you can see, the new GPO was denied because of the WMI Filter.
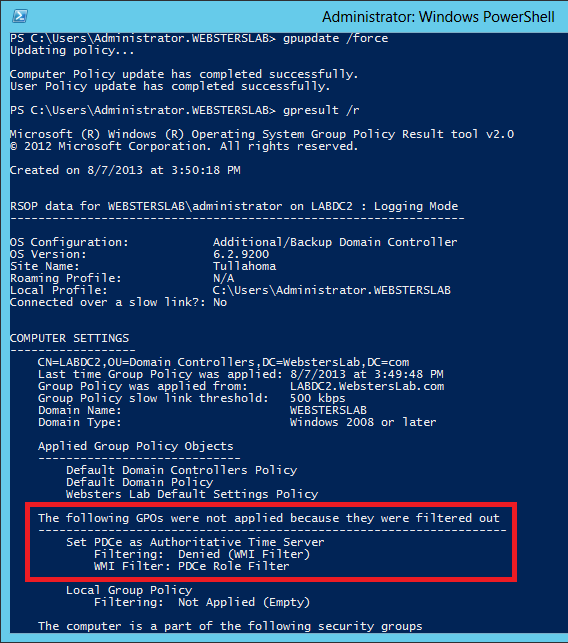
Figure 11 There you go. Now you can automate creating the Group Policy to set the Forest Root Domain’s PDCe as the authoritative time server for your AD Forest.
You can always find the most current script by going to https://www.carlwebster.com/where-to-get-copies-of-the-documentation-scripts/
Thanks
Webster
8 Responses to “Creating a Group Policy using Microsoft PowerShell to Configure the Authoritative Time Server”






October 22, 2014 at 8:13 am
Hi Carl,
Thank you very much for this script. Also, lots of thanks to Jeremy for his modifications. This script will allow me to automate a process that I have had to do manually for a couple of years now. I also modified the script in the following way:
If you are applying this script to a DC that is running on a virtual machine, you will want to change the SpecialPollInterval from the default to at most “900” (15 minutes) to minimize time skew. I added the following:
Set-GPPrefRegistryValue -Name $GPOName -Action Update -Context Computer `
-Key ‘HKLM\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpClient’ `
-Type DWord -ValueName ‘SpecialPollInterval’ -Value 900 | out-null
Also, if you are using a link that is unreliable, you may want the DC to use the gateway router as a secondary NTP server while the link is down. To do this, I added the following:
# Set this to the NTP Servers the PDCe will sync with
$TimeServers = “0.us.pool.ntp.org,0x9 1.us.pool.ntp.org,0xa 2.us.pool.ntp.org,0xa 3.us.pool.ntp.org,0xa”
$KnownGW = Read-Host ” Do you know the IP address of the Gateway Router? Y/N”
If($KnownGW -eq “Y”)
{
$GWIP = Read-Host ‘Please enter the Gateway IP Address’
$GW = $GWIP + “,0xa”
$TimeServers = $TimeServers + $GW
}
Else
{
Write-host “`n The PDCe will be configured with the US Pool NTP servers only`n`n”
}
Thought you might be interested in this.
Thanks again
-karl
January 14, 2014 at 8:53 am
Hi Carl,
I hope you don’t mind but I’ve enhanced your script to create both WMI Filters and GPOs and reposted it here: http://www.jhouseconsulting.com/2014/01/10/script-to-create-group-policy-objects-and-wmi-filters-to-manage-the-time-server-hierarchy-1153
Cheers,
Jeremy
January 15, 2014 at 7:30 am
I do not mind at all.
Webster
August 21, 2013 at 12:55 pm
Carl,
Great post Carl. I have been reading up on setting the authoritative NTP server manually vs. with a GPO for a new Windows Server 2012 domain. I did have one question. In a similar blog post by Jorge http://jorgequestforknowledge.wordpress.com/2010/09/26/configuring-and-managing-the-windows-time-service-part-2/ he uses two separate GPOs. One for all domain controllers, and the second for the one with the FSMO roles. If you only create one GPO as done above, do you risk having more than one authoritative time source? I was looking at the scenario of where you may transfer the FSMO roles to a new server, but the old server is still around. Will the registry settings remain on the old PDCe server even after it is no longer considered the domain master?
Thanks,
Andrew
August 22, 2013 at 7:18 am
Yes, I planned to write another article on that but the physical server that hosted my DC had processor issues and had to be rebuilt. I lost the VMs on it and never got to write the 2nd article. I will get that written, I hope, real soon.
Thanks
Webster
August 8, 2013 at 8:54 am
Masterful, Carl. Question though. What difference would it make if this was created Manually on the PDC? Besides the WMI filtering, is or are there any specific advantage to scripting the process?
Thanks,
Prince
August 8, 2013 at 9:02 am
None actually except now you have the process automated and documented.
You could also use a reg file, or have someone manually set the registry entries, or a vbscript, or….
Plus by using the WMI Filter, if you move the PDCe role to another server, at the next group policy refresh cycle (or running gpupdate /force or rebooting the new PDCe) the new PDCe instantly becomes the authoritative time server. Also, what happens if the PDCe is demoted and you were not aware that role was on the server? Using this the DC that receives the PDCe role will automatically become the new authoritative time server and you didn’t have to think about it.
The only reason I wrote this script (and went through the learning process) is because someone asked how to create the GPO using PoSH. I like learning and challenges that require me to learn.
Thanks
Webster
October 22, 2014 at 8:19 am
This will be a very valuable advantage to me. I have to travel around and perform assessments on our subordinate units to ensure that they have their PDCe NTP settings correct. Until now, I have had to provide written documentation and over the shoulder direction, which usually results in someone fat fingering something while creating the GPO or WMI filter. Now I can just give them the script and have them run it. Also, using Jeremy’s modification, I don’t have to copy the WMI module over, because the required piece is in the script.