-
What Happened to My Managed Service Accounts Container?
January 26, 2021
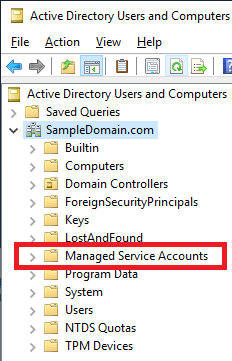
In Windows Server 2008 R2 Active Directory (AD), Microsoft introduced managed service accounts. If you create a new AD domain with Windows Server 2008 R2 or later, when you look in Active Directory Users and Computers (ADUC), you see a container named Managed Services Accounts, as shown in Figure 1.
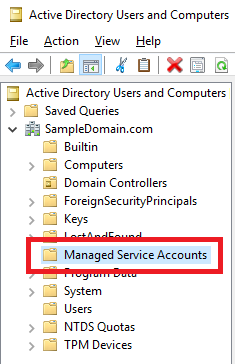
Figure 1 Some people mistakenly call this an Organizational Unit (OU), but it is a container. The Domain Controllers OU is the only OU created when you create an AD domain. You can see the difference in the icon between the Domain Controllers OU and the other items in the domain.
Enable Advanced Features in ADUC, as shown in Figure 2, by clicking View -> Advanced Features.
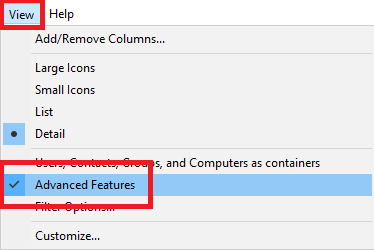
Figure 2 Right-click the Domain Controllers OU and click Properties, as shown in Figure 3.
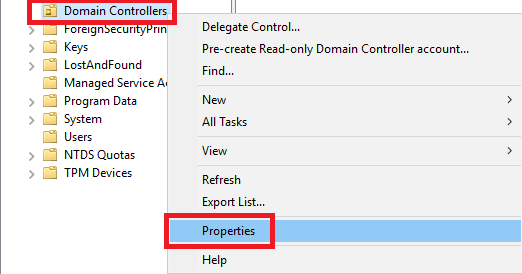
Figure 3 Click the Attribute Editor tab, and scroll down to find the objectCategory and objectClass attributes, as shown in Figure 4.
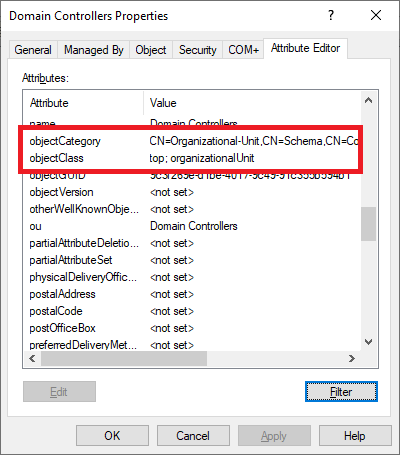
Figure 4 Those two attributes show Domain Controllers as an OU.
If you follow the same process for Managed Service Accounts, the two attributes show Managed Service Accounts as a container, as shown in Figure 5.
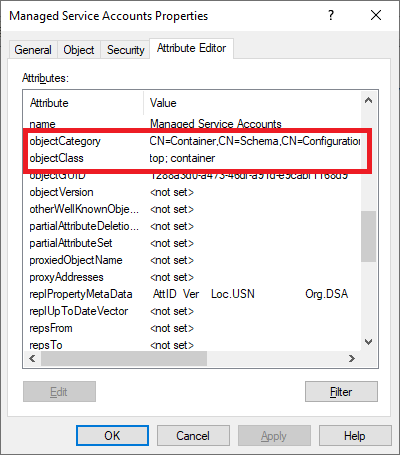
Figure 5 One other way to see the difference between a container and an OU is with the Group Policy Management Console (GPMC). As shown in Figure 6, if you open the GPMC and expand the domain, you only see OUs. There are no containers shown because you cannot directly link a Group Policy Object to a container.
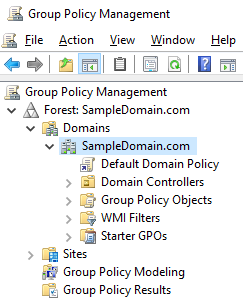
Figure 6 Back in ADUC, if you right-click any of the other containers, for example, Computers or Users, you see no Delete option, as shown in Figures 7 and 8.
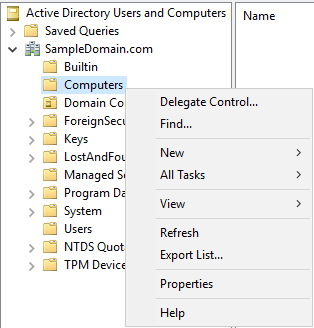
Figure 7 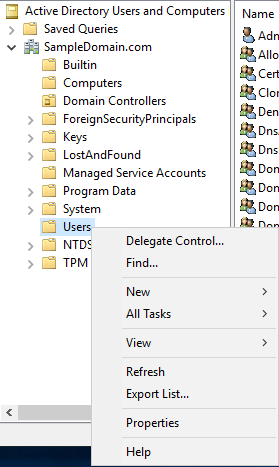
Figure 8 There is a Delete option when you right-click the Managed Service Accounts container, as shown in Figure 9.
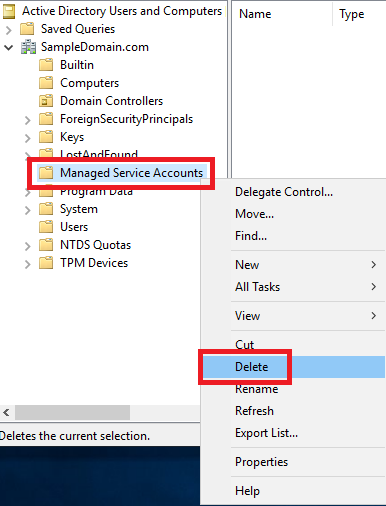
Figure 9 Because there IS a delete option, an admin can accidentally delete that container. The Managed Service Accounts container is not critical, which is probably why Microsoft allows for its deletion. If “someone” deletes the container, as shown in Figure 10, how do we get it back?
Figure 10 Recreating the Managed Service Accounts container is a simple process.
1. Open ADSIEdit
2. Right-click the ADSI Edit node and click Connect to…, as shown in Figure 11.
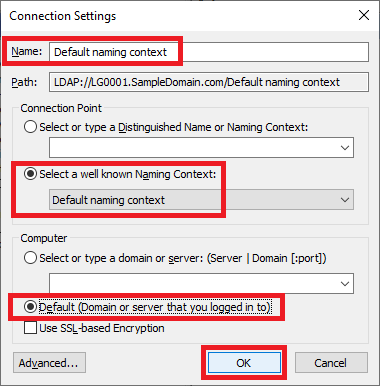
Figure 11 3. Name: Default naming context
Select a well known Naming Context: Default naming context
Select Default (Domain or server that you logged in to)
Click OK, as shown in Figure 12.
Figure 12
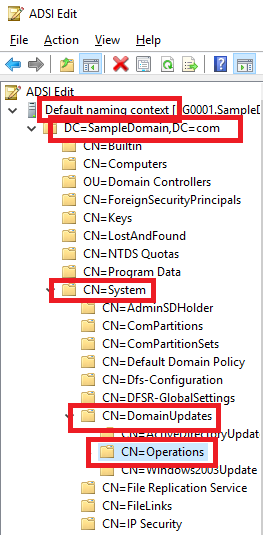
4. Drill down to Default naming context -> DC=<DomainName>,DC=<TLD> -> CN=System -> CN=DomainUpdates -> CN=Operations, as shown in Figure 13.
Figure 13
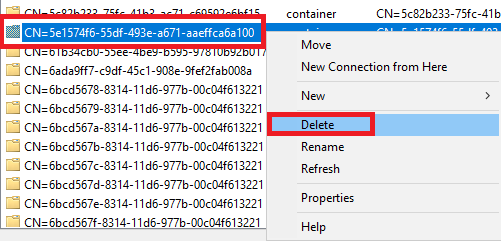
5. In the middle pane, right-click the item with the Name CN=5e1574f6-55df-493e-a671-aaeffca6a100 and click Delete, as shown in Figure 14.
Figure 14
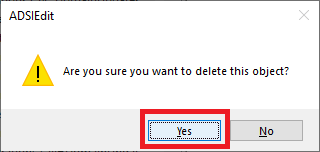
6. Click Yes to confirm the deletion, as shown in Figure 15.
Figure 15
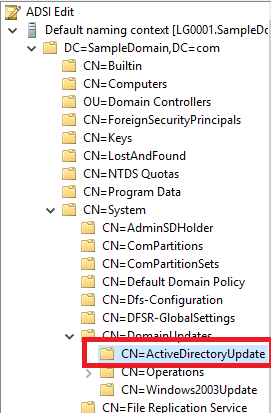
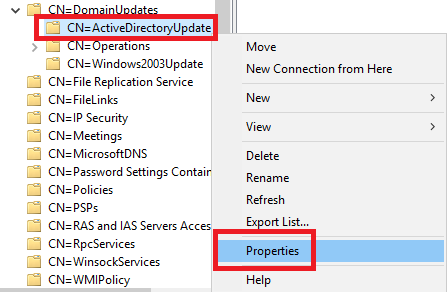
7. In the left pane, click on CN=ActiveDirectoryUpdate, as shown in Figure 16.
Figure 16
8. Right-click CN=ActiveDirectoryUpdate and click Properties, as shown in Figure 17.
Figure 17
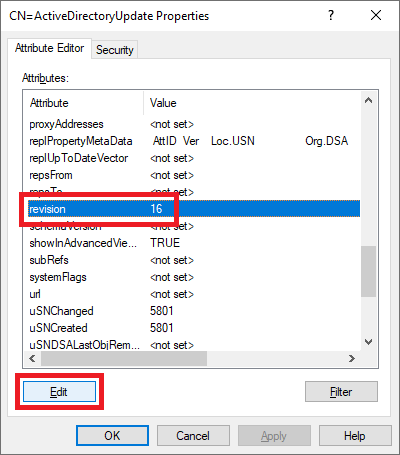
9. Scroll down and find the attribute named revision and click Edit, as shown in Figure 18.
Figure 18
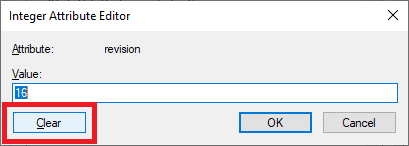
10. Click Clear, as shown in Figure 19.
Figure 19
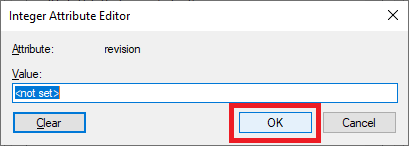
11. Click OK, as shown in Figure 20.
Figure 20
12. Close the dialog and exit ADSI Edit.
13. Mount your Server OS ISO.
14. Open an elevated command prompt.
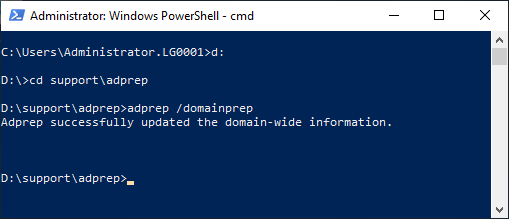
15. Change to the ADPrep folder, x:\support\adprep (where x: is the drive letter for the installation media) and run adprep /domainprep, as shown in Figure 21.
Figure 21
16. Refresh the ADUC console, and you see the Managed Service Accounts container, as shown in Figure 22.
Figure 22
Now you can get back to doing whatever it is you wanted to do with managed service accounts.
Thanks
Webster
12 Responses to “What Happened to My Managed Service Accounts Container?”






June 27, 2024 at 5:12 pm
Thank you!
December 5, 2023 at 12:03 pm
Saved me! Thank you!!
November 28, 2023 at 8:00 am
Question, your article states the following
” If you create a new AD domain with Windows Server 2008 R2 or later, when you look in Active Directory Users and Computers (ADUC), you see a container named Managed Services Accounts, as shown in Figure 1.”
What if your domain has been upgraded from the days of Windows 2000? Our AD does not shown the container but I would figure after all the forest and domain upgrades it should have appeared.
November 28, 2023 at 11:05 am
Check this article:
Dude, Where’s My Managed Service Accounts?
November 28, 2023 at 12:21 pm
Thanks. I have seen this article before but am confused as to what this object is.
CN=d262aae8-41f7-48ed-9f-35-56-bb-b6-77-57-3d
Would you happen to know what this object is for?
I also contacted Microsoft and they stated not to delete this. I will go with your recommendation.
December 22, 2023 at 8:40 am
No, I don’t know what it is for. I can’t find anything on it or the other. You could rename it and after running “ADPrep /domainPrep”, you can see if the two CNs were recreated.
Webster
July 25, 2023 at 5:00 am
Thanks for the information, it also worked for me.
In my case, with several domain controllers in different sites, we needed to wait for the ADSI edit changes to replicate to the other domain controllers, after step 12.
If we tried to run adprep /domainprep before replication, it failed with error “Domain-wide information has already been updated. [Status/Consequence] Adprep did not attempt to rerun this operation.”
After the ADSI edit changes were replicated to all domain controllers, the adprep /domainprep ran successfully “Adprep successfully updated the domain-wide information.”
And then we needed to wait again, for the replication to run to the other domain controllers, for the “Managed Service Accounts” container to show up.
July 25, 2023 at 6:43 am
Do have Change Notification enabled? Microsoft recommends doing this change as it makes AD treat all DCs as if they were in one site. Greatly reduces your AD convergence time.
Get-ADObject -Filter ‘objectClass -eq “siteLink”‘ -SearchBase (Get-ADRootDSE).ConfigurationNamingContext | Set-ADObject -Replace @{Cost=100;ReplInterval=15;Options=5}
https://learn.microsoft.com/en-us/archive/blogs/ashleymcglone/report-and-edit-ad-site-links-from-powershell-turbo-your-ad-replication
Webster
June 28, 2023 at 9:55 am
thanks
March 25, 2023 at 7:02 am
Using Powershell, why does Get-ADObject not return gMSAs? ADUC lists them as ‘computer’ objects, but Get-ADComputer also will not return them. Get-ADGroup and Get-ADGroupMember will both show them as members. But you’d have to already know what they are ahead of time to identify them in a script, and say, retrieve their properties. You must use Get-ADService Account to retrieve them.
March 25, 2023 at 8:03 am
My AD mentors tell me that AD PoSH cmdlets are not the best way to get AD data. That is why Michael B. Smith’s handprints are all over the AD doc script.
Webster
June 7, 2022 at 12:41 pm
Thank you!
This worked perfectly!