[Updated 8-Nov-2021]
With the domain controllers built, Active Directory (AD) configured, and the Certificate Authority Server configured, the next step is to create the initial settings within Group Policy Objects (GPOs). The primary purpose of the Group Policy engine is to apply policy settings to computers and users in an AD domain, enabling administrators to automate one-to-many management of settings to users and computers. Using Group Policy as a settings delivery engine simplifies administrative tasks and reduces IT costs. Administrators can efficiently implement security settings and enforce IT policies consistently across a given site, domain, or range of organizational units.
Group Policy consists of many pieces and parts, and there are tens of thousands of possible settings and options available. Here are a few helpful links to help you better understand Group Policy.
- Group Policy Overview
- Group Policy Planning and Deployment Guide
- What are Group Policy and Group Policy Objects?
- Group Policy Settings Storage (PDF)
One of my Group Policy mentors, Darren Mar-Elia, has several Group Policy training videos on Pluralsight.
- Group Policy Fundamentals
- Windows Server 2019: Group Policy Fundamentals
- Play by Play: Group Policy Best Practices with Darren Mar-Elia
- Best Practices for Group Policy Deployment and Management
- Designing and Managing a Group Policy Deployment
My other Group Policy mentor, Jeremy Moskowitz, has a Group Policy book you should read (I have all six editions). He also has a Group Policy training course which has hands-on labs. The course is in-person or online (labs are the same).
If you want a deep dive into all the technical details of Group Policy, please see Group Policy Protocols Overview and click the link to download a PDF or Word document. That is a great document to read if you have insomnia.
Default GPOs
When we created the AD domain in Part 14, the process created two default group policies: the Default Domain Policy and the Default Domain Controllers Policy.
Paraphrased from Group Policy Protocols Overview.
Default Domain Policy: A default GPO created and linked to the domain whenever a server becomes the first domain controller in a domain. It has the highest precedence of all GPOs linked to the domain, and it applies to all users and computers in the domain. The Default Domain Policy GPO is generally used to manage default account settings, although there are exceptions to this practice. For other areas of policy management, you can create new GPOs; however, some policy settings are best configured at the domain level, and there are no restrictions against doing so.
Default Domain Controllers Policy: A default GPO created and linked to the “Domain Controllers” OU whenever a server becomes the first domain controller in a domain. This GPO represents the default policy applied to all domain controllers in the Domain Controllers container.
In an article for the Dcgpofix utility, Microsoft makes statements about what those two GPOs should contain.
Default Domain Policy: As a best practice, you should configure the Default Domain Policy GPO only to manage the default Account Policies settings, Password Policy, Account Lockout Policy, and Kerberos Policy.
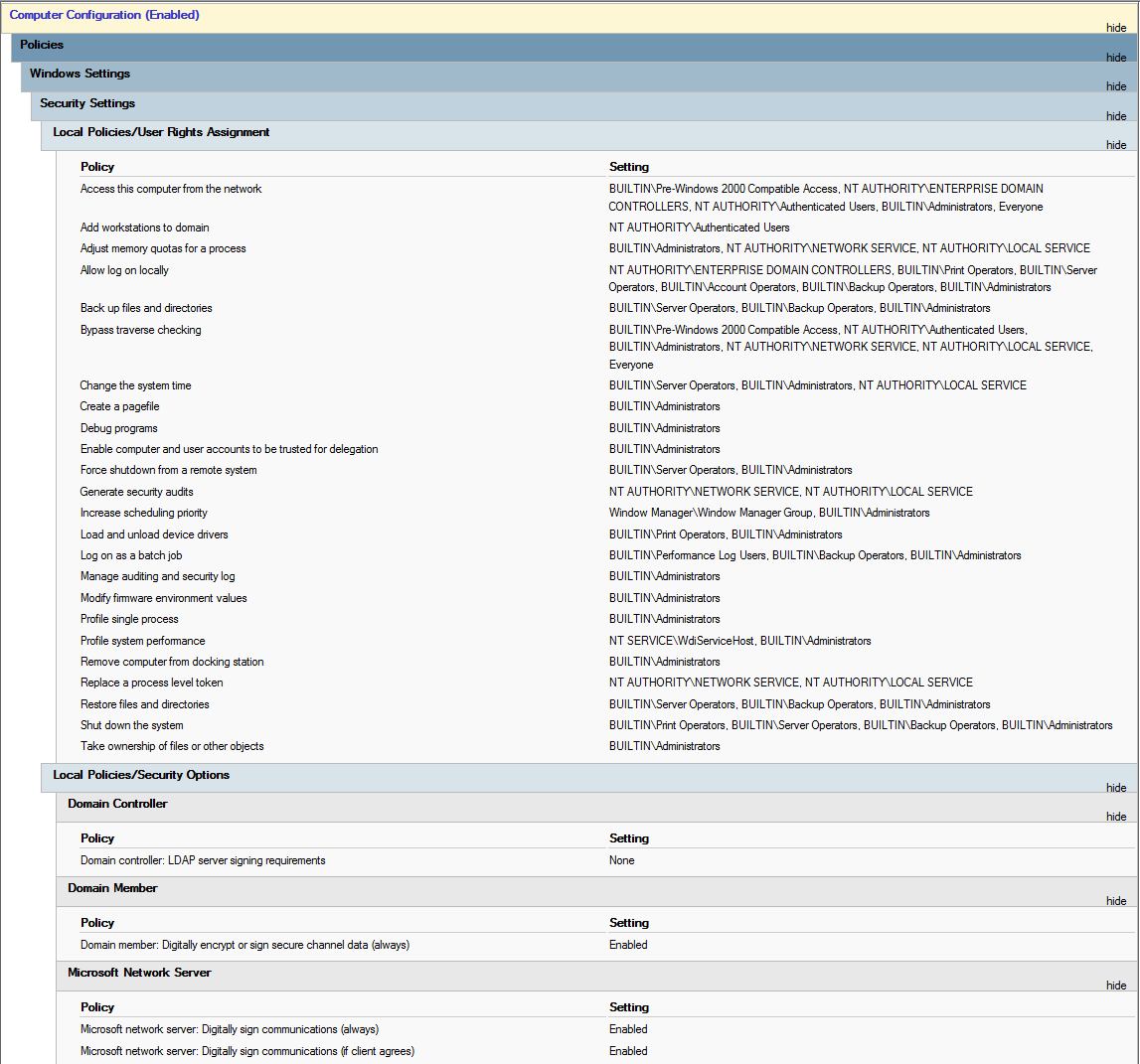
Default Domain Controllers Policy: As a best practice, you should only configure the Default Domain Controllers Policy GPO to set user rights and audit policies.
I recommend you limit the changes made to the two default GPOs to specifically the areas instructed. If you wish to create new and existing “other policy items”, then instead, create new GPOs as needed to control your required domain and domain controller policy settings. If you ever find yourself needing to run the dcgpofix utility, you lose any changes made to those original built-in GPOs. This includes password settings and account lockout settings in the Default Domain Policy.
Figure 1 shows the settings in my Default Domain Policy. User Configuration settings should not exist in this GPO.
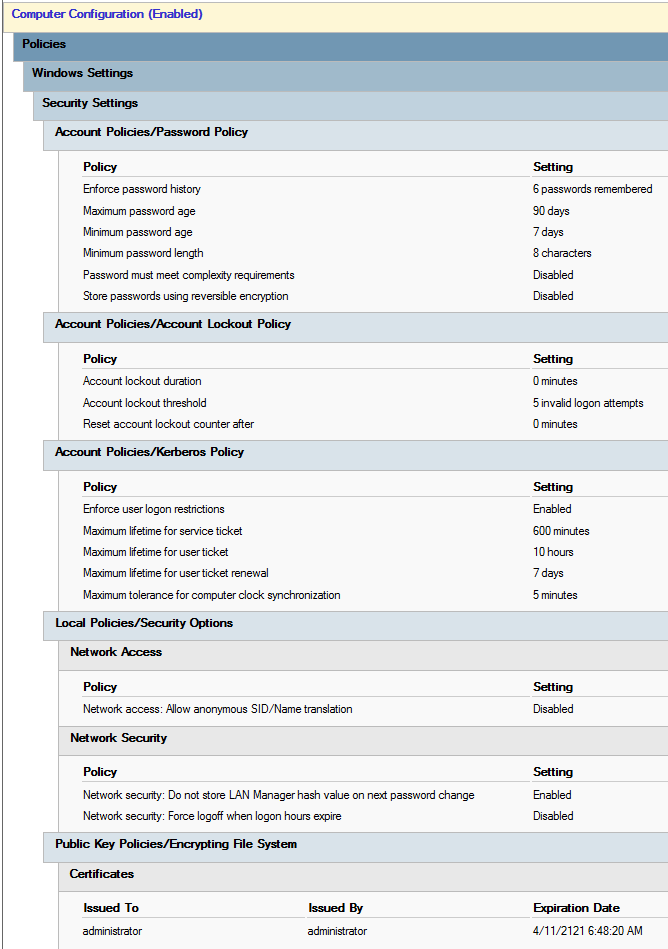
Figure 2 shows the settings in my Default Domain Controllers Policy. User Configuration settings should not exist in this GPO.
Authoritative Time Server GPO
Time is one of the most critical components that always makes AD work and work correctly. AD cannot work correctly if time synchronization is off between domain controllers and member computers. For example, in Kerberos V5 (which AD uses), computers that are more than five minutes out of sync may not authenticate by default. Another example is replication; AD uses timestamps to resolve replication conflicts.
I use the script from Jeremy Saunders to automate the creation and maintenance of time server settings.
Script to Create Group Policy Objects and WMI Filters to Manage the Time Server Hierarchy – http://www.jhouseconsulting.com/2014/01/10/script-to-create-group-policy-objects-and-wmi-filters-to-manage-the-time-server-hierarchy-1153
There is one change needed in the script. The script uses servers from pool.ntp.org for Australia, where Jeremy is based.
Change this line:
$TimeServers = "0.au.pool.ntp.org,0x8 1.au.pool.ntp.org,0x8 2.au.pool.ntp.org,0x8 3.au.pool.ntp.org,0x8"
To:
$TimeServers = "north-america.pool.ntp.org,0x8"
Note: Use the servers for your geolocation. You can also use dedicated hardware or a network appliance as your time source. Use the IP address. For example, “10.20.30.40, 0x8”
After you download and modify Jeremy’s script, save it on the first domain controller in c:\Scripts, as shown in Figure 3.
Open an elevated PowerShell session and enter the following commands, as shown in Figure 4.
cd c:\Scripts .\CreateTimeServerGPOs.ps1
Press Enter and the script runs, as shown in Figure 5.
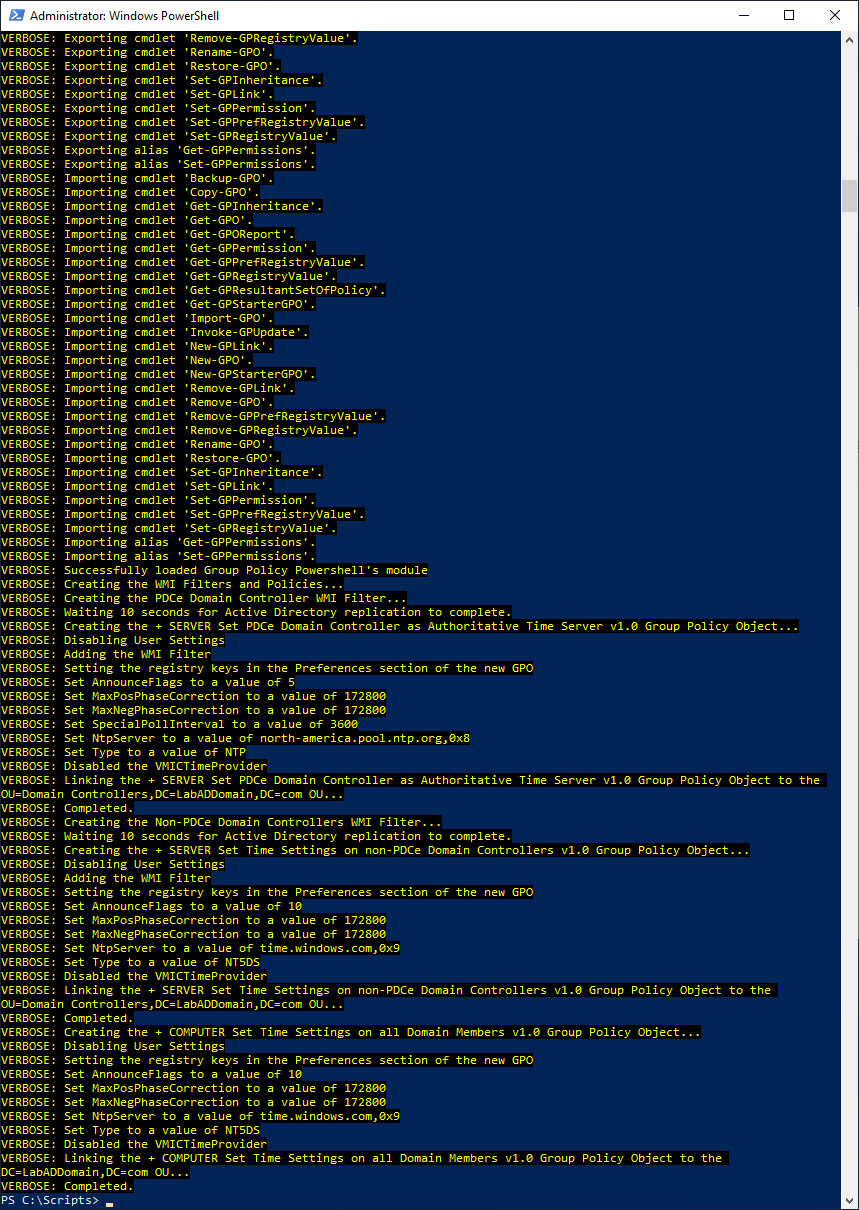
What did the script do?
Open the Group Policy Management Console (GPMC) by typing in gpmc.msc in the elevated PowerShell window and pressing Enter.
Expand the GPMC to view more content.
Expand the Forest.
Expand Domains.
Expand the Domain.
Expand Domain Controllers.
Expand Group Policy Objects.
Expand WMI Filters.
Figure 6 shows the three GPOs and the two WMI filters that Jeremy’s script created.
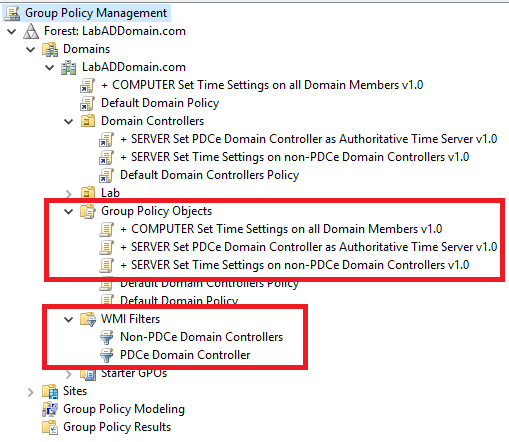
What these GPOs and WMI filters do is make your life easy. You never have to worry about ensuring the DC that holds the PDCe FSMO role is configured correctly as the authoritative time server. You never have to worry about transferring or seizing the PDCe FSMO role to another DC or about configuring that DC as the authoritative time server. You never have to worry if all the other servers and computers in your domain are configured correctly for the AD time hierarchy. All these concerns are handled by the GPOs that Jeremy’s script created.
To verify the GPOs are working correctly, open the Event Viewer on all three servers we have in the lab at this point.
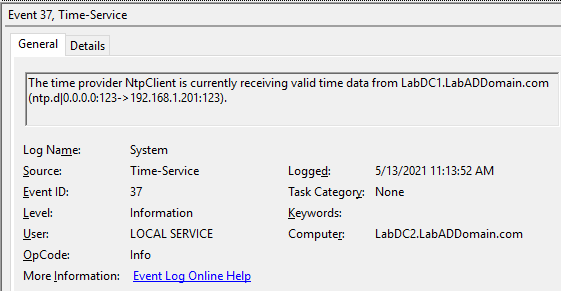
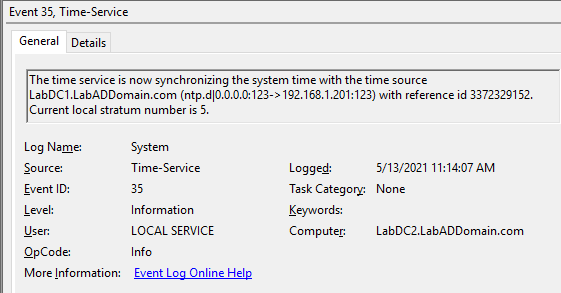
On the PDCe DC, look for Event IDs 37 and 35, as shown in Figures 7 and 8.
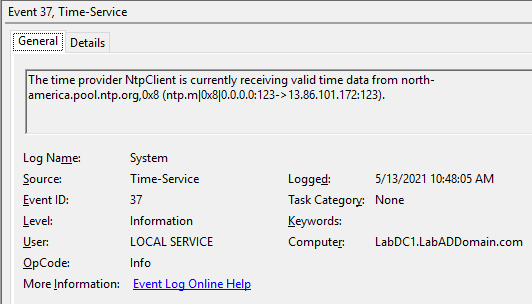
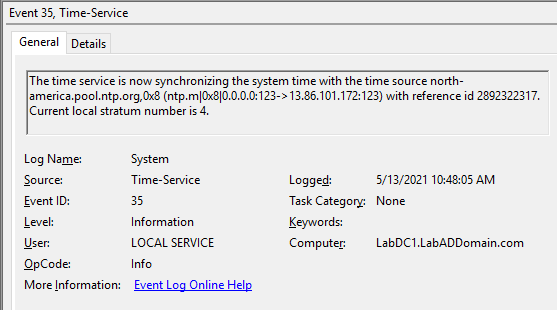
Wait several minutes, then on the other DC, look for Event IDs 37 and 35, as shown in Figures 9 and 10.
Note: If you don’t want to wait, restart the Windows Time service.
PowerShell:
Stop-Service W32Time Start-Service W32Time
Command Prompt:
net stop w32time && net start w32time
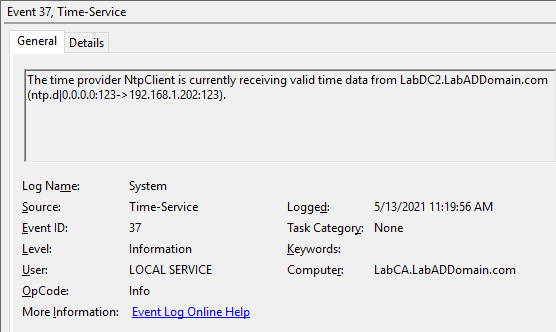
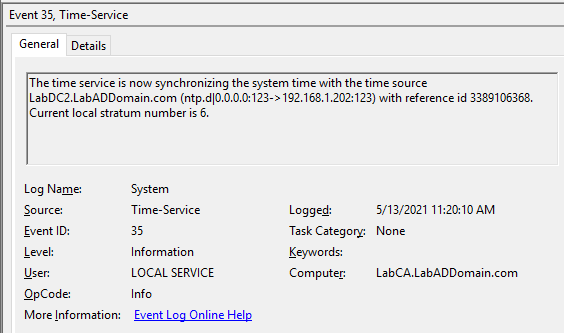
On the CA, after waiting several minutes, look for Event IDs 37 and 35, as shown in Figures 11 and 12.
Install Root and Intermediate Certificates
So far, we reviewed the two default policies and let PowerShell do all the work for the authoritative time server policy. We manually create the following policy.
I recommend creating all GPOs in the Group Policy Objects node in the GPMC. Why? If you create and link a GPO at any level, that GPO is immediately LIVE; and any changes you make could apply to whatever computers or users reside in the level you are working at any time. That is dangerous if you work on a policy and it’s incomplete. Or if you create or edit a security or lockdown policy and you make an inadvertent change. I prefer to create GPOs first, then after completing the work, link the GPO to the appropriate level(s), which puts its proposed actions into practice.
In the GPMC, right-click Group Policy Objects and click New, as shown in Figure 13.
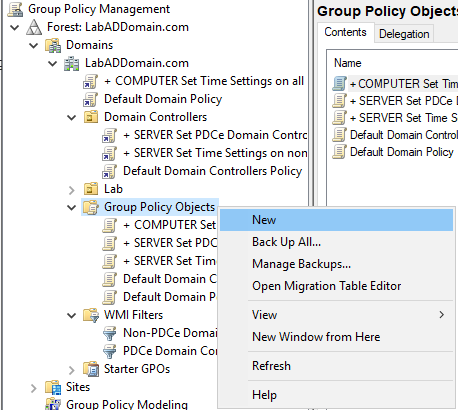
Give the new policy a meaningful Name and click OK, as shown in Figure 14.
I have recommendations I make to customers for how to name GPOs.
- Convention: Policy Add-in Type (C or U or CU)-Policy Name
- C = computer
- U = User
- CU = Computer and User
- Policy Name – Whatever makes sense but should be meaningful to the use of the GPO
- The policy name must not contain any of the following reserved characters:
- < – less than
- > – greater than
- : – colon
- ” – double-quote
- \ – backslash
- / – forward slash
- | – The pipe symbol
- ? – question mark
- * – asterisk
- Examples:
- (C) – Loopback Replace
- (U) – IE Site to Zone Mapping
- (CU) – Google Chrome Settings
- (C) – Domain Password Policy – Enforced
Why the restriction on characters allowed in the GPO name? You can create a GPO with those characters in the GPO name. The problem comes when using PowerShell to create GPO backups and reports. PowerShell cannot create folders and files for a GPO with any reserved characters in the GPO’s name. Please see this article from Microsoft. Naming Files, Paths, and Namespaces
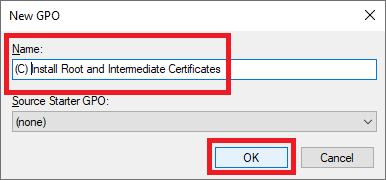
Right-click the new GPO and click Edit…, as shown in Figure 15.
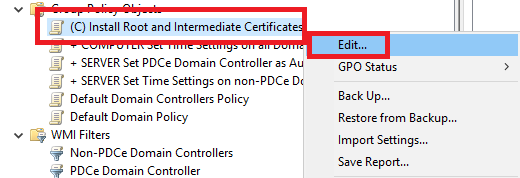
In the left pane, expand Computer Configuration, Policies, Windows Settings, Security Settings, Public Key Policies, and in the right pane, click Certificate Services Client – Auto-Enrollment, as shown in Figure 16.
Double-click Certificate Services Client – Auto-Enrollment and change Configuration Model to Enabled, as shown in Figure 17.
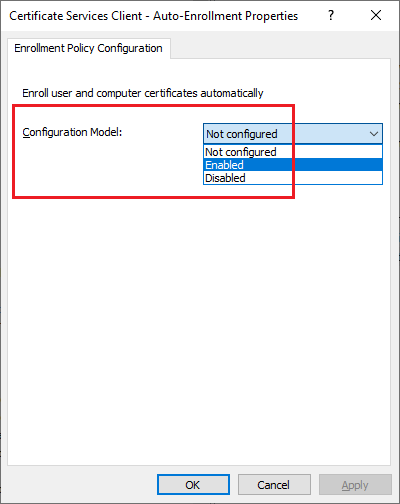
Select Renew expired certificates, update pending certificates, and remove revoked certificates, and Update certificates that use certificate templates, and click OK, as shown in Figure 18.
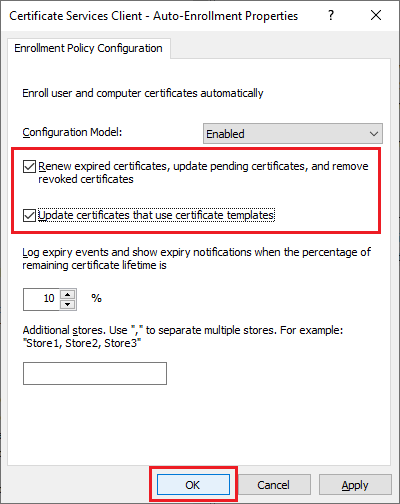
Right-click Trusted Root Certification Authorities and click Import…, as shown in Figure 19.
Click Next, as shown in Figure 20.
Click Browse…, as shown in Figure 21.
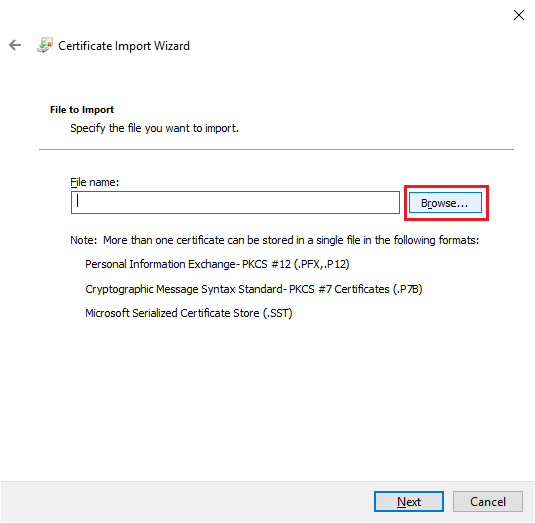
Browse to the folder created on the CA server, click the exported Root Certificate file, and click Open, as shown in Figure 22.
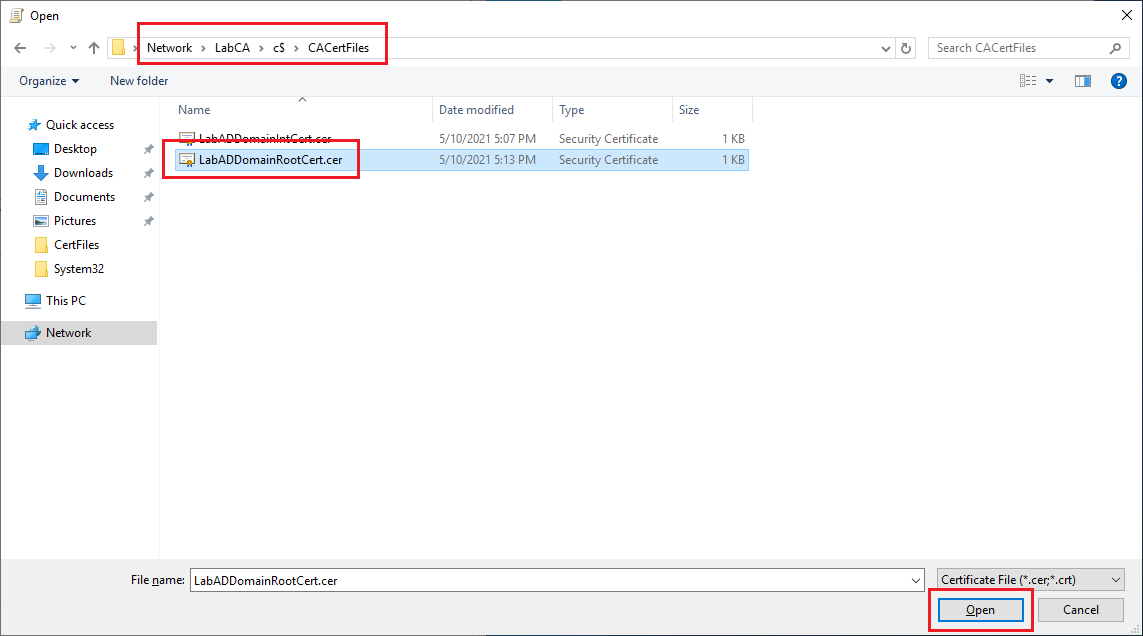
Click Next, as shown in Figure 23.
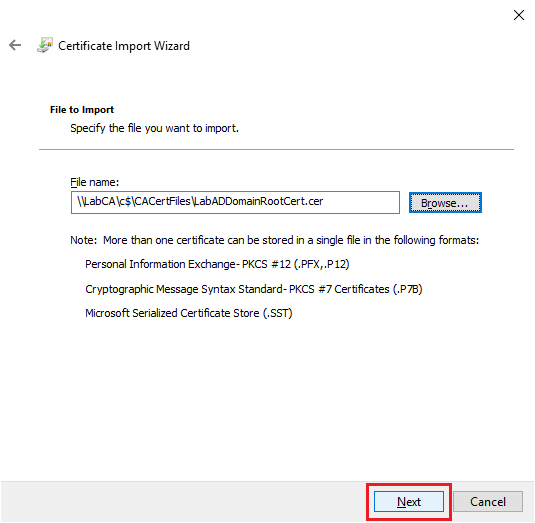
Click Next, as shown in Figure 24.
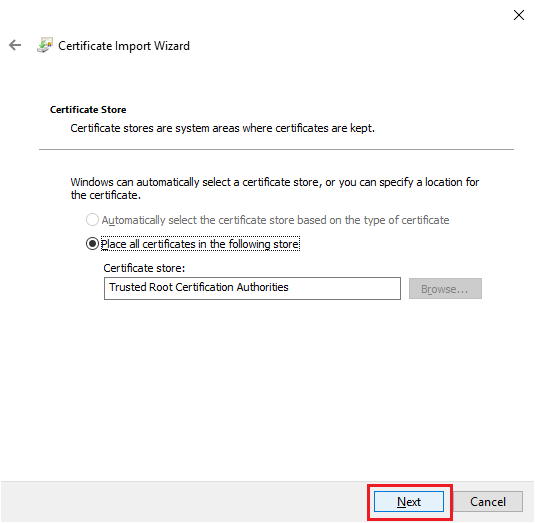
Click Finish, as shown in Figure 25.
Click OK, as shown in Figure 26.
In the right pane, you see the Root Certificate added, as shown in Figure 27.
Right-click Intermediate Certification Authorities and click Import…, as shown in Figure 28.
Click Next, as shown in Figure 29.
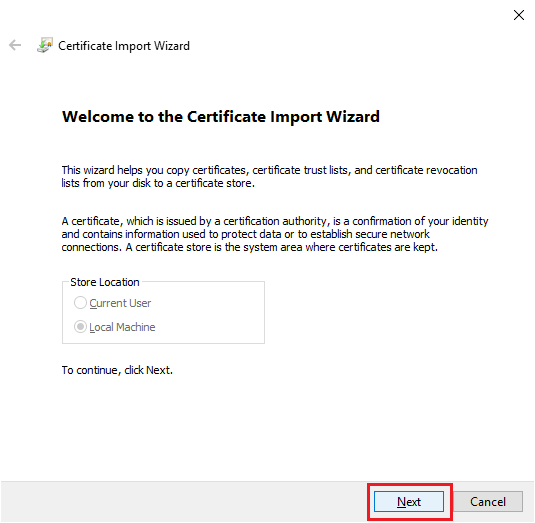
Click Browse…, as shown in Figure 30.
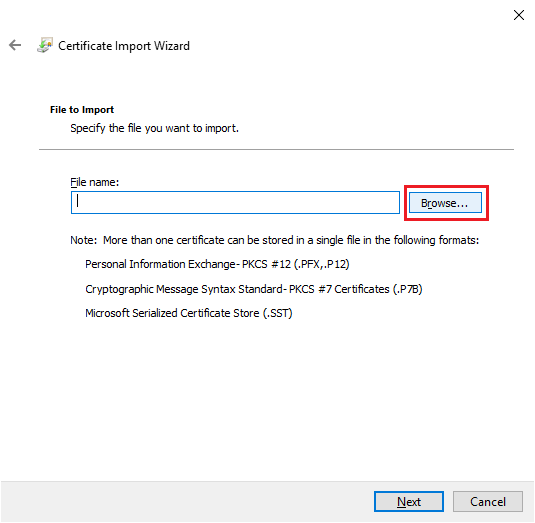
Browse to the folder created on the CA server, click the exported Intermediate Certificate file, and click Open, as shown in Figure 31.
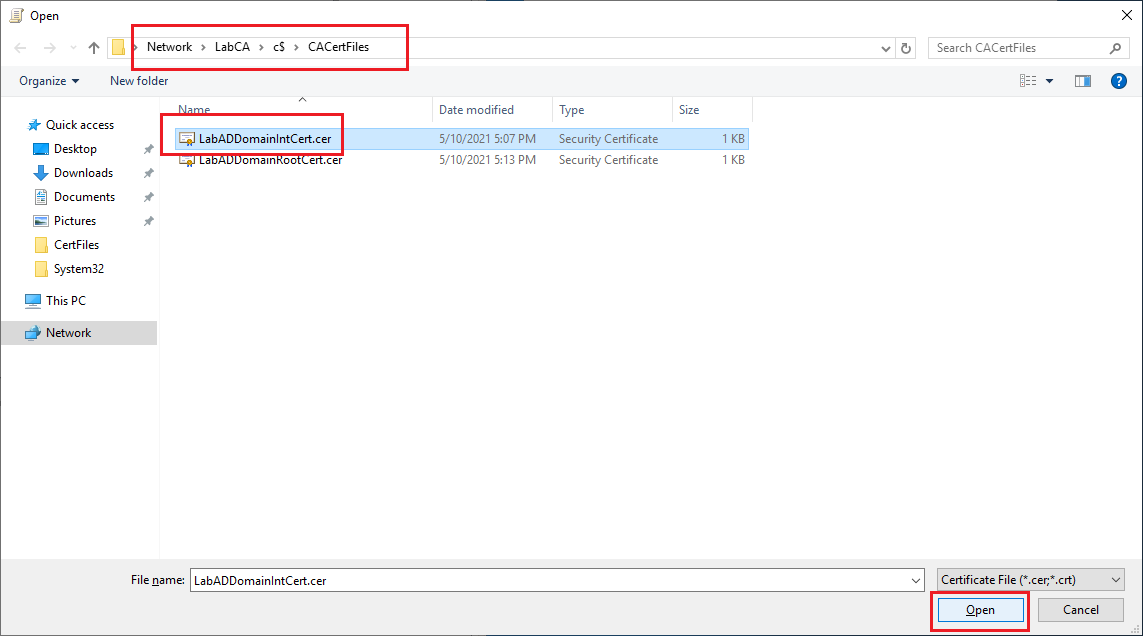
Click Next, as shown in Figure 32.
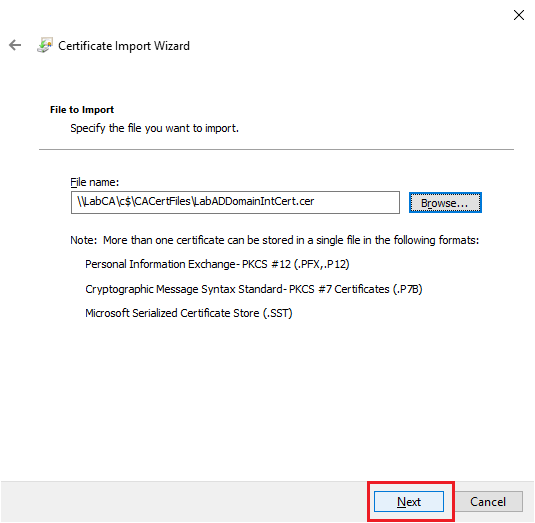
Click Next, as shown in Figure 33.
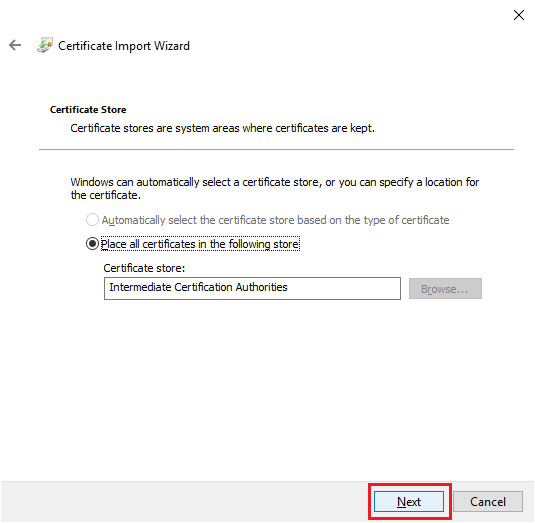
Click Finish, as shown in Figure 34.
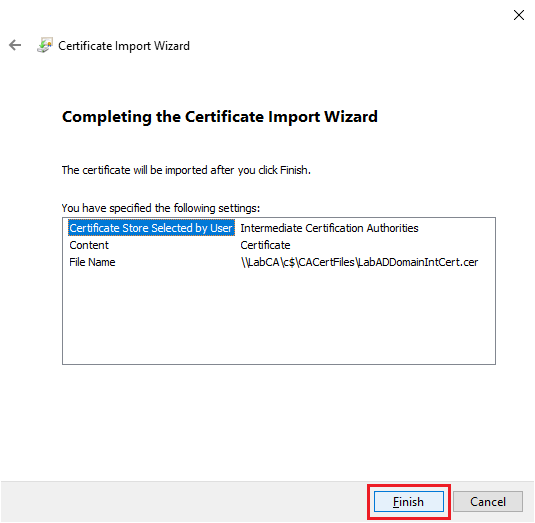
Click OK, as shown in Figure 35.
In the right pane, you see the Intermediate Certificate added, as shown in Figure 36.
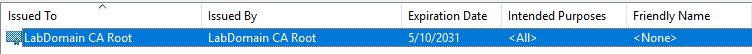
Exit the Group Policy Management Editor (not the GPMC).
I want this certificate group policy to apply to all computer accounts in the Lab OU since all computer accounts, other than domain controllers, must exist in that OU tree.
Right-click the Lab OU and click Link an Existing GPO…, as shown in Figure 37.
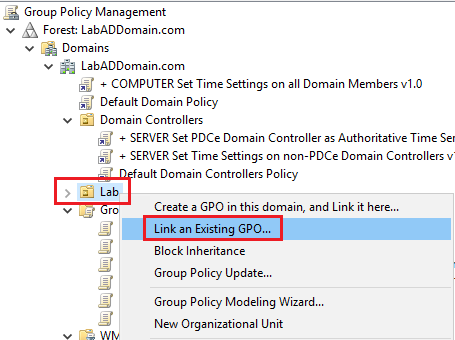
Select the new GPO and click OK, as shown in Figure 38.
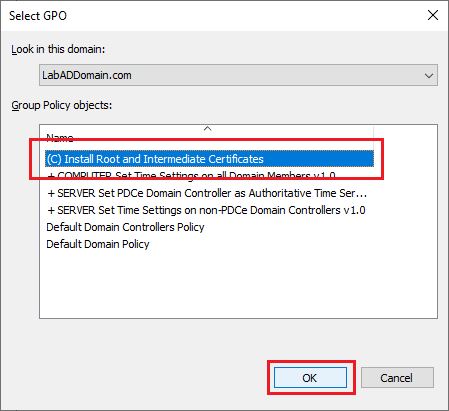
Expand the Lab OU, and see the certificate group policy is at the top level of the Lab OU tree, as shown in Figure 39. This means that as computers join the domain and are placed in the Lab OU tree, they automatically receive this group policy on the first reboot.
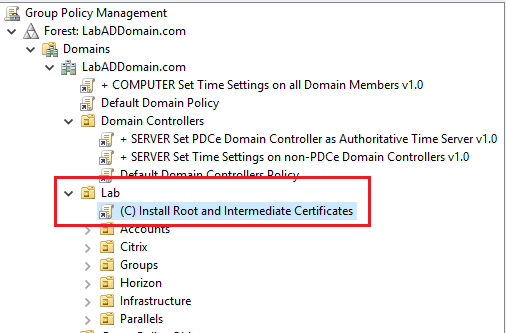
Lab Defaults
Now you know how to create, edit, and link a GPO. For this GPO, I give you the recommended settings I use in my lab. You can decide which settings make sense for you, plus any additional settings you may want to add. Remember, there are thousands of settings from which to choose.
This GPO contains computer settings I apply to every computer in the domain. You can find all of the settings here in Computer Configuration / Policies.
Windows Settings | Security Settings | System Services | DNS Client. Check “Define this Setting” and then specify “Automatic.” Leave other settings as-is. [Webster: I have seen customers have issues where the DNS Client Service somehow gets set to disabled. If this service is disabled, there could be name resolution issues.]
Administrative Templates | Control Panel | Regional and Language Options | Handwriting personalization | Turn off automatic learning. Set to Enabled.
Administrative Templates | Network | Link-Layer Topology Discovery | Turn on Mapper I/O (LLTDIO) driver. Set to Enabled and select Allow operation while in domain. [Webster: Without this configured, no computer in the domain can browse and find the File Server.]
Administrative Templates | Network | Link-Layer Topology Discovery | Turn on Responder (RSPNDR) driver. Set to Enabled and select Allow operation while in domain. [Webster: Without this configured, no computer in the domain can browse and find the File Server.]
Administrative Templates | System | Server Manager | Do not display Initial Configuration Tasks window automatically at logon. Set to Enabled. [Webster: Reduces the clutter on a computer’s screen at startup.]
Administrative Templates | System | Server Manager | Do not display Server Manager automatically at logon. Set to Enabled. [Webster: Reduces the clutter on a computer’s screen at startup.]
Administrative Templates | Windows Components | Add features to Windows 10 | Prevent the wizard from running. Set to Enabled.
Administrative Templates | Windows Components | Camera | Allow Use of Camera. Set to Disabled. [Webster: None of my hosts or VMs have cameras.]
Administrative Templates | Windows Components | Cloud Content | Do not show Windows tips. Set to Enabled.
Administrative Templates | Windows Components | Cloud Content | Turn off Microsoft consumer experiences. Set to Enabled.
Administrative Templates | Windows Components | Connect | Don’t allow this PC to be projected to. Set to Enabled.
Administrative Templates | Windows Components | Data Collection and Preview Builds | Allow commercial data pipeline. Set to Disabled.
Administrative Templates | Windows Components | Data Collection and Preview Builds | Allow Telemetry. Set to Enabled and set the Options to 3 – Full.
Administrative Templates | Windows Components | Data Collection and Preview Builds | Do not show feedback notifications. Set to Enabled.
Administrative Templates | Windows Components | Desktop Gadgets | Turn off desktop gadgets. Set to Enabled.
Administrative Templates | Windows Components | HomeGroup | Prevent the computer from joining a homegroup. Set to Enabled.
Administrative Templates | Windows Components | News and interests | Enable news and interests on the taskbar. Set to Disabled. [Webster: If you do not see this setting, wait until you finish the Central Store section and then see Group configuration: news and interests on the Windows taskbar.]
Administrative Templates | Windows Components | OneDrive | Prevent the usage of OneDrive for file storage. Set to Enabled. [Webster: I don’t use Onedrive. If you use OneDrive, do not configure this setting.]
Administrative Templates | Windows Components | Search | Allow Cortana. Set to Disabled. [Webster: I don’t care for Cortana. If you use Cortana, do not configure this setting.]
Administrative Templates | Windows Components | Security Center | Turn on Security Center (Domain PCs only). Set to Disabled. [Webster: If you like the Security Center, do not configure this setting.]
Administrative Templates | Windows Components | Store | Turn off the Store application. Set to Enabled. [Webster: I don’t use the Store in lab VMs.]
Administrative Templates | Windows Components | Windows Defender SmartScreen | Explorer | Configure Windows Defender SmartScreen. Set to Disabled. [Webster: I find SmartScreen slows down Windows File Explorer. If you use SmartScreen, do not configure this setting.]
Administrative Templates | Windows Components | Windows Defender SmartScreen | Microsoft Edge | Configure Windows Defender SmartScreen. Set to Disabled. [Webster: I find SmartScreen slows down internet browsing. If you use SmartScreen, do not configure this setting.]
Administrative Templates | Windows Components | Windows Ink Workspace | Allow Windows Ink Workspace. Set to Disabled.
Administrative Templates | Windows Components | Windows PowerShell | Turn on Script Execution. Set to Enabled and set the Execution Policy to Allow all scripts. [Webster: I do a lot of PowerShell scripting and run PowerShell scripts from other friends. If you do not trust every PowerShell script, you should consider setting the Execution Policy to Allow local and remote signed scripts. That means every PowerShell script that doesn’t come from your computer requires a digital signature.]
Administrative Templates | Windows Components | Windows Remote Shell | Allow Remote Shell Access. Set to Enabled.
Administrative Templates | Windows Components | Windows Update | Configure Automatic Updates. Set to Disabled.
Administrative Templates | Windows Components | Windows Update | Windows Update for Business | Manage preview builds. Set to Enabled and Set the behavior for receiving preview builds to Disable preview builds.
Administrative Templates | Windows Components | Windows Update | Windows Update for Business | Select the target Feature Update version. Set to Disabled.
To go along with these two settings, we need to configure three Firewall settings.
- Administrative Templates | Network | Link-Layer Topology Discovery | Turn on Mapper I/O (LLTDIO) driver
- Administrative Templates | Network | Link-Layer Topology Discovery | Turn on Responder (RSPNDR) driver
In the Group Policy Management Edit (GPME), go to Windows Settings | Security Settings | Windows Defender Firewall with Advanced Security and expand Windows Defender Firewall with Advanced Security, as shown in Figure 40.
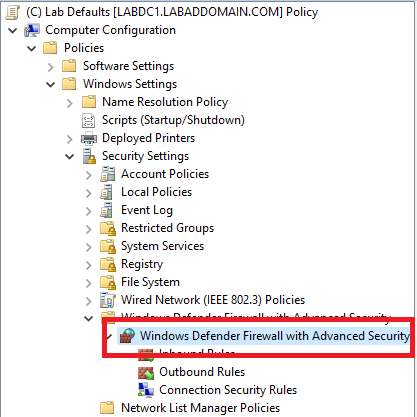
Right-click Inbound Rules and click New Rule…, as shown in Figure 41.
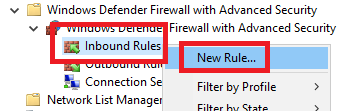
Select Predefined from the dropdown list, select File and Print Sharing, and click Next, as shown in Figure 42.
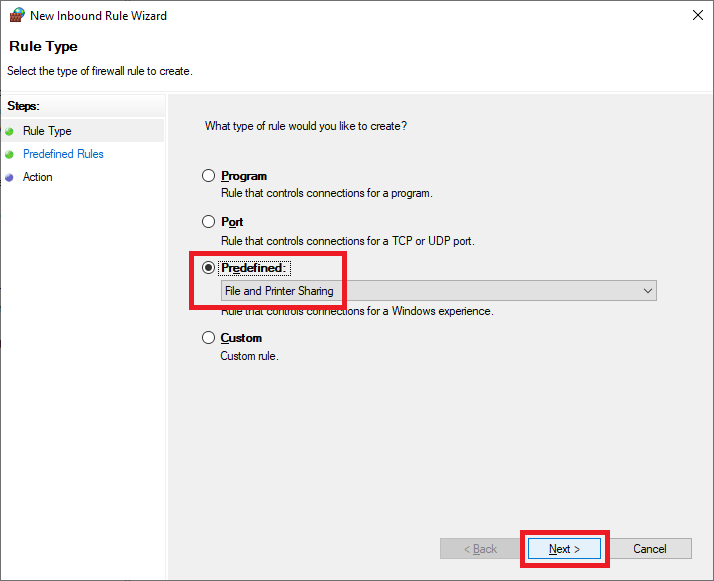
Click Next, as shown in Figure 43.
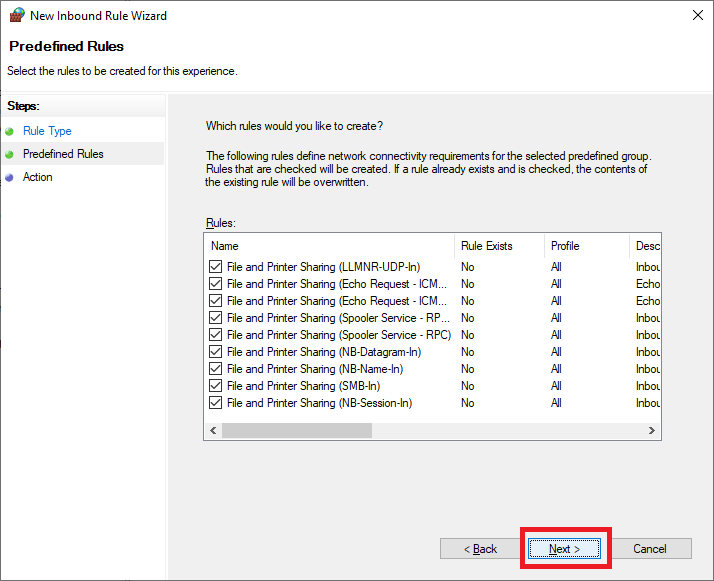
Select Allow the connection and click Finish, as shown in Figure 44.
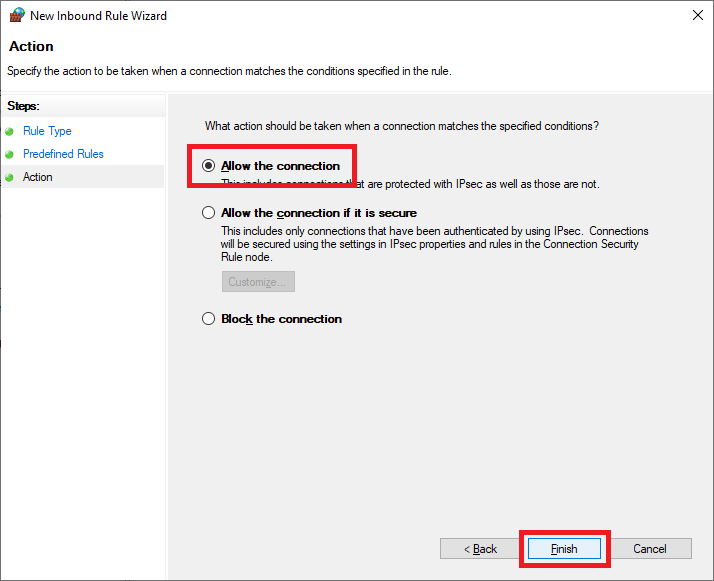
Create another Inbound Rule.
Select Predefined from the dropdown list, select Network Discovery, and click Next, as shown in Figure 45.
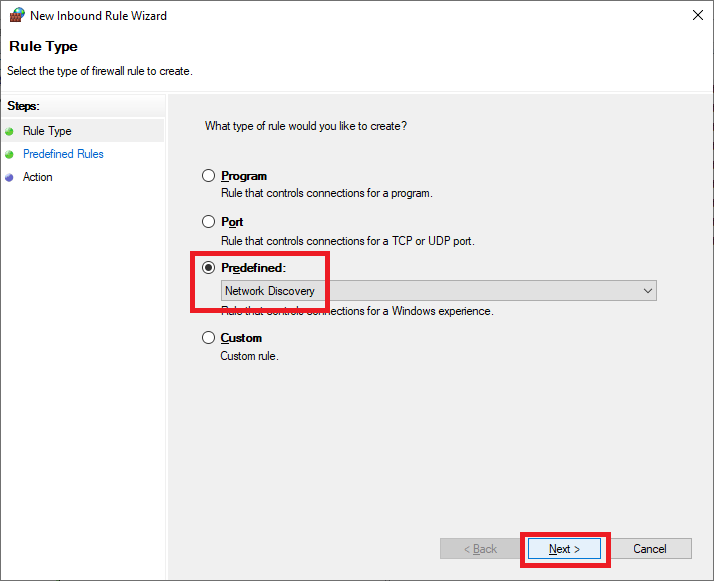
Click Next, as shown in Figure 46.
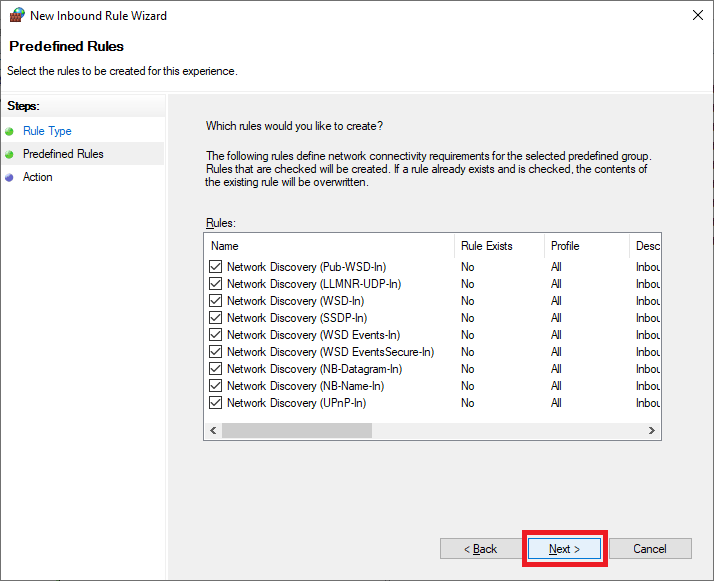
Select Allow the connection and click Finish, as shown in Figure 47.
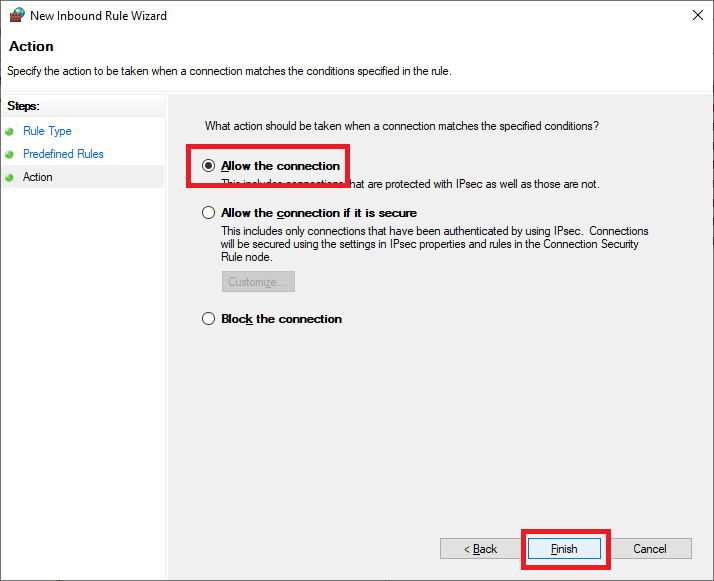
Create an Outbound Rule.
Select Predefined from the dropdown list, select File and Print Sharing, and click Next, as shown in Figure 48.
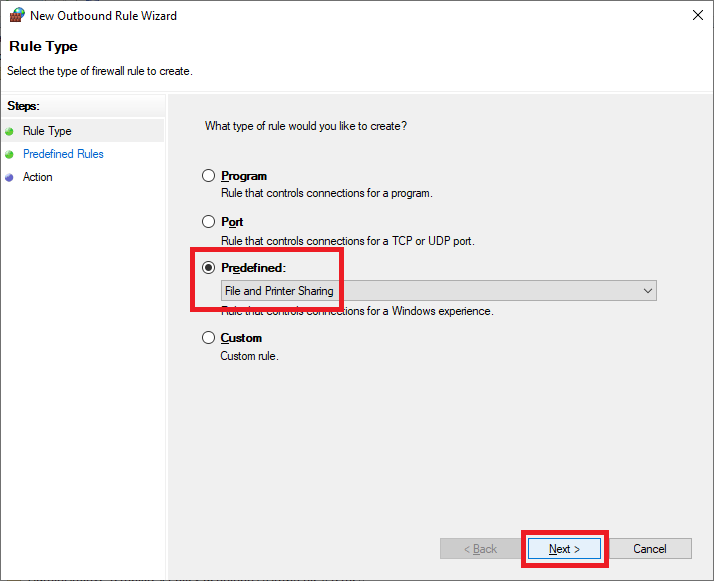
Click Next, as shown in Figure 49.
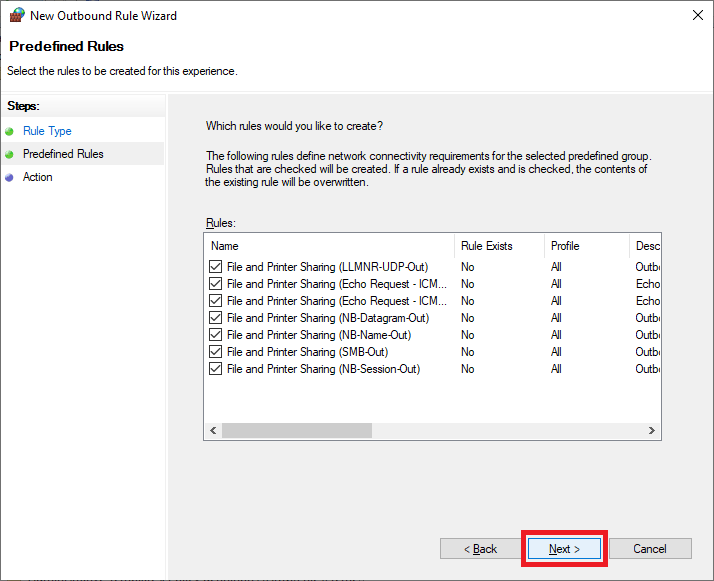
Select Allow the connection and click Finish, as shown in Figure 50.
Exit the GPME (not the GPMC).
Testing the Lab Defaults GPO
Before we go headlong and test out the Lab Defaults GPO we just created together, let’s do a quick sanity check.
First: Did you remember to create the policy in the Group Policy Objects node?
Second: Did you give the GPO a name recognizable by someone else later? In my example, I named my policy (C) Lab Defaults.
Lastly: Now that I finished configuring the GPO, I was sure to link my GPO at the domain level, as shown in Figure 51.
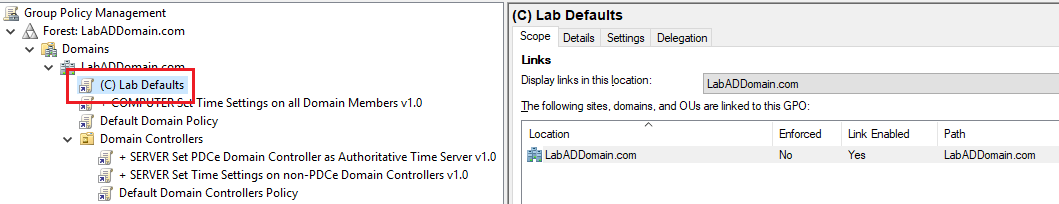
Be sure you have all three things set and ready to go before proceeding.
Now you’re ready to do a simple test of the settings within this GPO.
To do this, log off the CA or second DC and then log back in. One of the settings we specified was to disable the Server Manager from showing expressly. When you log in, the Server Manager should now be absent.
Tip: If Server Manager still appears, either restart the VM or do a Right-click Start, Run, gpupdate. Then log off and back on to see if it took effect. Gpupdate is a command-line utility from Microsoft that comes with all versions of the Windows operating system to refresh the Group Policy engine on the client. There are many ways of running gpupdate. As an administrator, you can even force a group policy refresh remotely using PowerShell or the GPMC.
We have all the GPOs we need at this time.
Exit the GPMC.
Central Store
Most Group Policy configuration settings that administrators use are in the Administrative Templates section of the Group Policy Management Editor. Microsoft divides Administrative Templates files into .admx files and language-specific .adml files for use by Group Policy administrators. To take advantage of the benefits of .admx files, you must create a Central Store in the sysvol folder on a Windows domain controller.
What is the Central Store? That link has links to Microsoft-supplied admx files for most versions of Windows. There are also vendor-supplied admx files for Google Chrome, Firefox, and many other products. With all the admx files available, especially for Microsoft Office, tens of thousands of settings are available for use with group policy.
With all the admx files available, it makes sense to have a central place to store the admx and related adml files. That is the purpose behind the Central Store.
Tip: For a video overview on creating a central store, see this video by Jeremy Moskowitz.
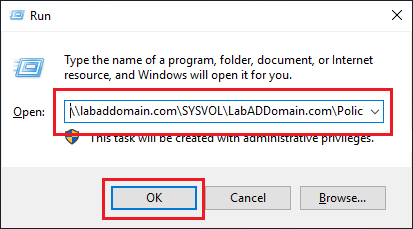
On the first domain controller (the one with the PDCe FSMO role), right-click Start, Run, as shown in Figure 52.
Type in \DomainName\SYSVOL\DomainName\Policies and click OK, as shown in Figures 53 and 54.
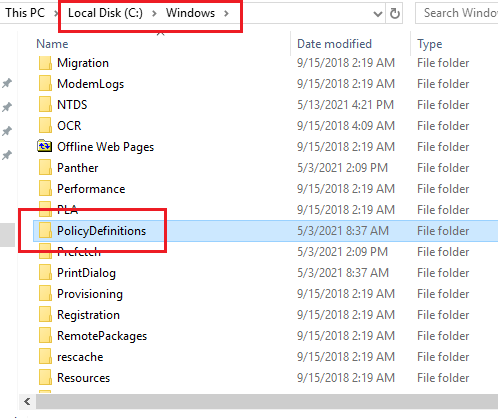
Open another File Explorer, go to C:\Windows, and scroll down to PolicyDefinitions, as shown in Figure 55.
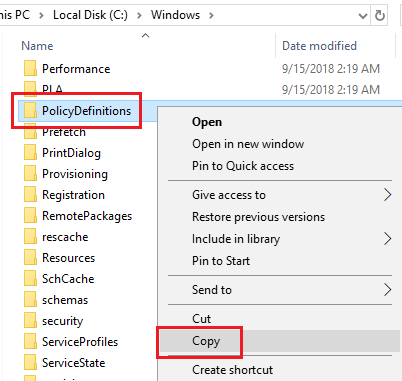
Right-click the PolicyDefinitions folder and click Copy, as shown in Figure 56.
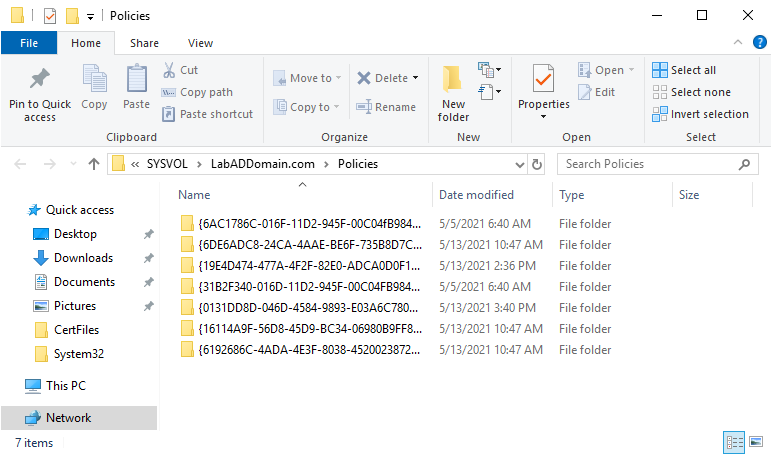
In the other File Explorer window showing \DomainName\SYSVOL\DomainName\Policies, right-click in an empty space and click {Paste, as shown in Figure 57.
The C:\Windows\PolicyDefinitions folder and its contents are copied, as shown in Figures 58 through 60.
When you download additional admx and adml files, copy the admx file(s) to the PolicyDefinitions folder and the adml file(s) to the language-specific folder(s) under the PolicyDefinitions folder.
The SYSVOL folder tree replicates to all DCs. On both DCs, open File Explorer and browse to C:\Windows\SYSVOL\sysvol\<DomainName>\Policies. You see that each DC in the domain has a copy of the PolicyDefinitions folder.
As you add admx and adml files to one DC’s C:\Windows\SYSVOL\sysvol\<DomainName>\Policies\PolicyDefinitions folder, SYSVOL replication copies the new file(s) to all other DCs in the domain.
Backup Group Policy
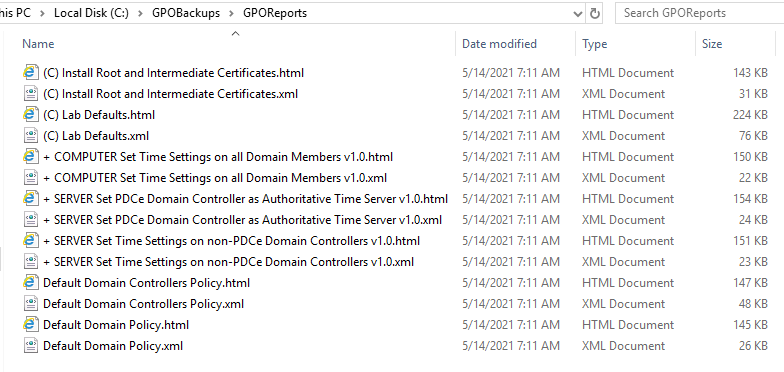
Creating GPO backups is easy because I created a free script that backs up and creates HTML and XML reports for all GPOs.
Get-Help .\Get-GPOBackupAndReports.ps1 -full
Running the script is easy. First, make a folder to place the zip files, backups, and reports and run the script, as shown in Figure 61.
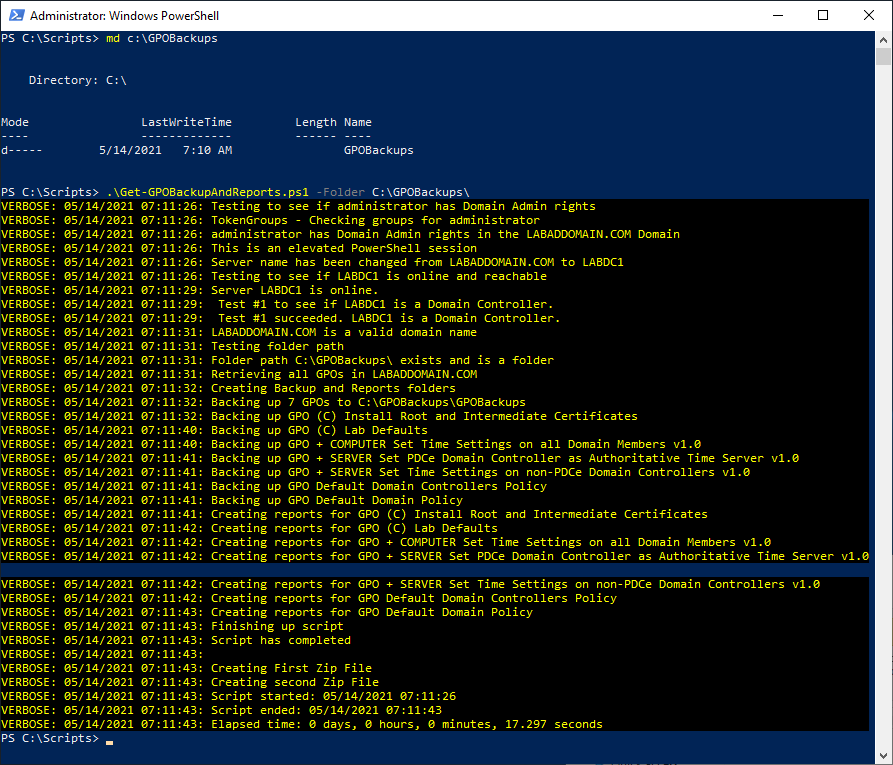
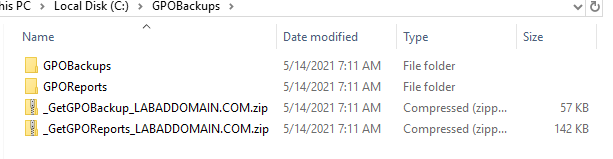
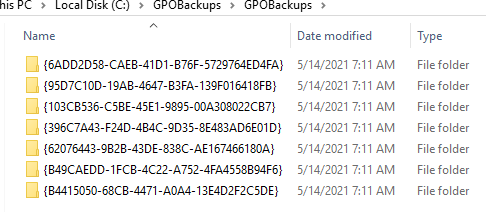
The folder I created, C:\GPOBackups, contains all the files created by the script, as shown in Figures 62 through 64.
Up next: Additional vCenter Configuration
Hello,
Picture 42, 48 and 43 49
There are in both file and printer sharing
Best regards
Tobias
One is an Inbound rule and the other is an Outbound rule
OK, but this is difficult to see from the picture. In picture 41 you create inbound rules. There is missing a picture from outbound rules.
If you click an image, it should open up in a new tab. I don’t think are any missing images.
Webster
Hello Carl,
In your Labbuild Build GPO article you have add two time the same pictures for creating the firewall rules.
Best regards
Tobias
Which Figure is the duplicate?
Webster